How to add TACACS+ to your Cisco logins
How to add TACACS+ to your Cisco logins
In the interest of fairness, since I recently blogged about RADIUS authentication, I thought it would be a good idea to talk about TACACS+ as well. You will find that the configuration steps are quite similar, but the resulting functionality with TACACS+ exceeds the capabilities offered by RADIUS. The objective of this blog is not to show all the features that TACACS+ provides, but just to give a few screenshots on basic TACACS+ authentication.
For instructor-led Cisco CCNA Certification training, see our course schedule.
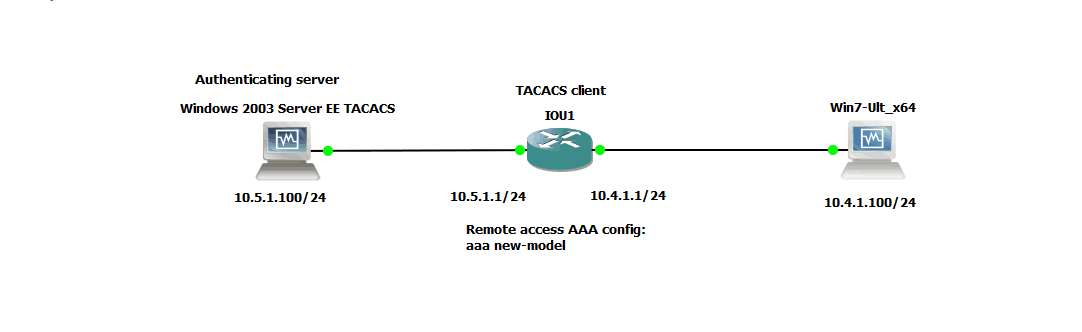
My topology is shown in figure 1:
Figure 1
Here the Cisco device fulfills the role of the client, while I have a Server 2003 box as the authenticating server. Yes I could have built a newer server than 2003, but just to have screen shots of basic authentication did not seem justification enough, since I already had this one.
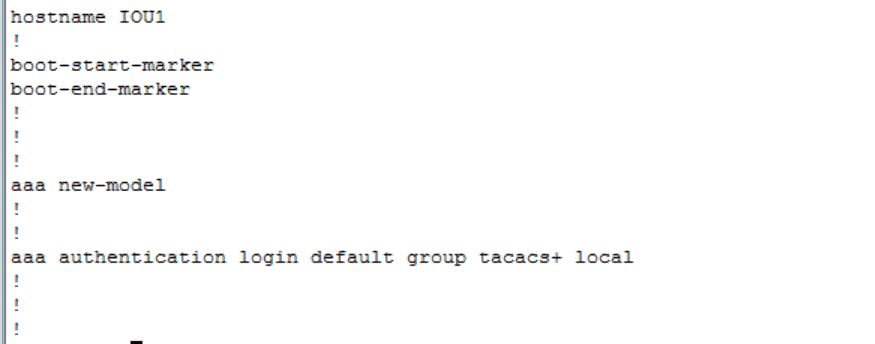
Let’s see the config on the Cisco device which will cause it to forward authentication attempts:
Figure 2
You will notice that much like the aaa authentication …radius command, I have added the keyword ‘local’ to the end of the command. This important step will allow an authorized user to access the device even if the authenticating server should be unreachable.
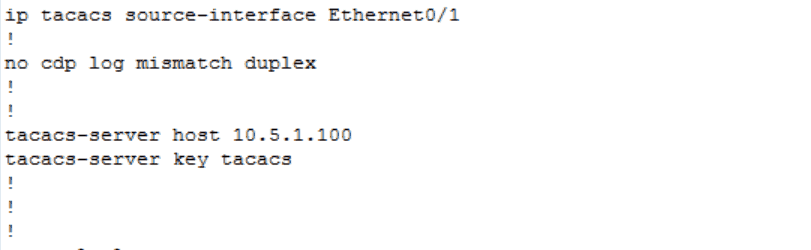
Figure 2 shows the minimum aaa commands required to make this function. Now for the tacacs-specific commands:
Figure 3
Figure 3 shows that I have identified the source interface for the TACACS+ requests, and I have identified the destination and key for the requests as well. Figure 1 shows that the 10.5.1.100 address belongs to my authenticating server.
Now to test this. I will attempt to log in to the Cisco device from my Windows 7 client using a valid username/password combination and a reachable authenticating server:
Figure 4
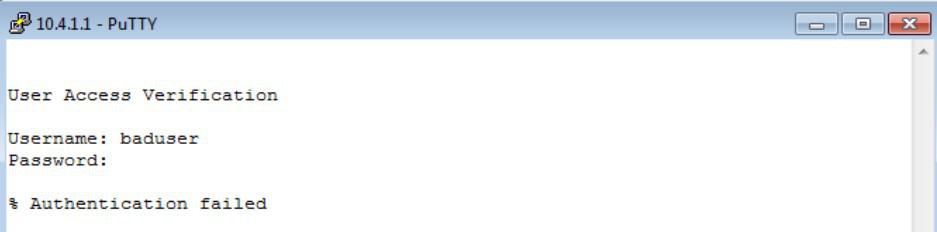
Voila! I have authenticated successfully using TACACS+. Another test that would assuage a network admin’s nerves regarding security is to test authentication with known bad credentials to verify failure. Let’s check:
Figure 5
Failed as expected. The last verification step I will show today is that of using what should be good credentials but the TACACS+ authenticator is unreachable. In that case, the device should fail back to the locally configured user database. Let’s verify this as well. I will disable the network card on my Server 2003 box to cause the TACACS+ requests to be ignored. Watch what happens:
Figure 6
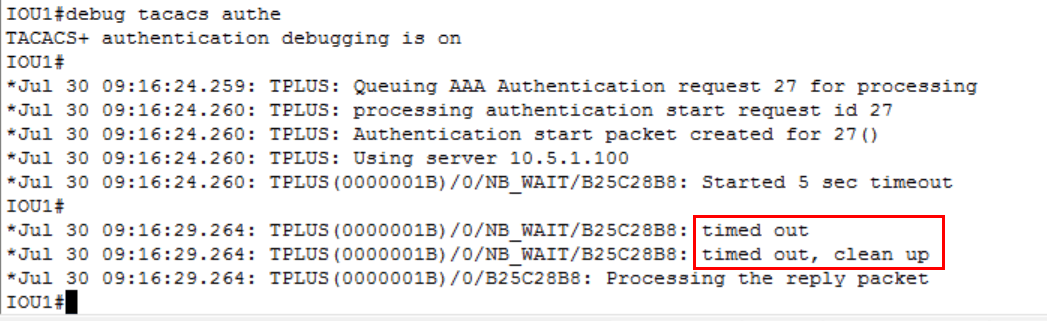
Figure 6 shows successful access to the device, but how do I know that the authenticating server did not provide this access? I ran debug tacacs authentication on my router. Let’s examine the output:
Figure 7
Notice in figure 7 that the client attempted to contact the authenticating server, but the request timed out. Since I had a locally configured username and password that matched my attempt, access was granted.
As mentioned, there is far more that TACACS+ can do for you, right down to controlling a user’s experience by permitting or denying individual commands. That is far deeper than one needs to delve when seeking the CCNA R&S certification, but it never hurts to a least familiarize oneself with the overall concepts.
If you have questions or comments, please feel free to post them!
Until next time….
Mark Jacob
Cisco and CompTIA Network + Instructor – Interface Technical Training
Phoenix, AZ
You May Also Like
aaa authentication, authentication, authenticator, Cisco, Cisco client, debug tacacs, RADIUS, TACACS+, TACACS+ authentication
A Simple Introduction to Cisco CML2
0 3896 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 642 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 727 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments