Access Management Control in IT is not just about the tools!
Access Management Control in IT is not just about the tools!
In today’s changing and complex environment, there is a growing concern and much discussion around the role of access management and the validity of the controls in place to support overall security and compliance initiatives. Often times, organizations fall short of their access control goals, but why? Simply deploying the latest in tools and technologies is only one ingredient to the overall process of access management. New threats, technologies and compliance rules stress the use of controls. Add to this to the fear of failing an audit or worse yet encountering an unauthorized access can shift focus away from the organization’s real objective which is to protect the its key asset – information. What practices should you be considering and possibly deploying to meet the needs of this evolving process? Make no mistake, access management has a multitude of models, frameworks and advice regarding how best to deploy and control it but there is one thing in common: access management is a discreet process that must be treated as such.
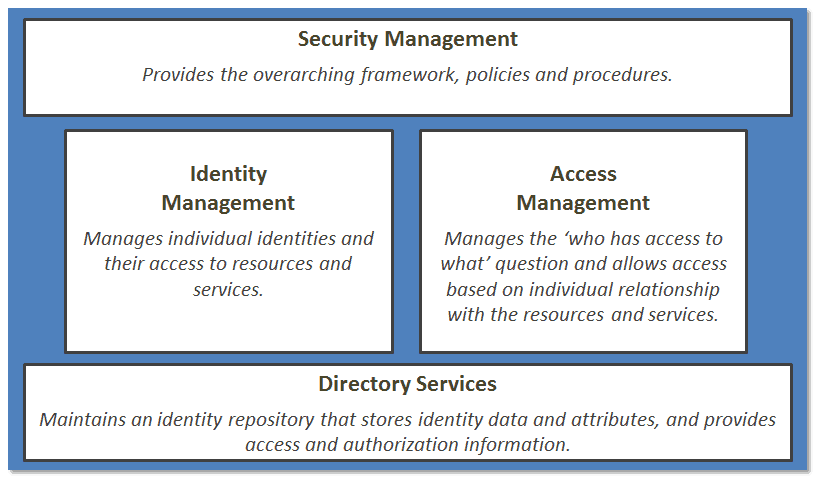
The model below illustrates that although this is a separate process, it has key relationships with other areas. At the risk of sounding cliché, “the whole is greater than the sum of its parts” is a perfect way to summarize that although you can deploy each area, they are often inert without the others. Each of the areas below should be viewed as a holistic approach, as opposed to focusing on individual areas.
Although I stress access management as a separate process, I have found it much more efficient to consider identity and access combined into a single process, since they have a VERY tight relationship, which I hope to illustrate in a few paragraphs. I call this IAM, or Identity and Access Management. You may have heard of the term before (I don’t want to claim IAM as my term, it has been used often in our industry). IAM means many things to different organizations. Within the context of my perspective here, we will refer to the following definitions:
Access Management: The process of granting authorized users the right to use a service, while preventing access to non-authorized users. This is also referred to as rights management or identity management in some organizations.
Access Controls: The security features that control how users and systems communicate and interact with one another.
Identity Management: A broad term to include the use of different products to identify, authenticate, and authorize users through automated means.
Authentication: Method of proving the identity. Something a person is, has, or does. Includes biometrics, passwords, passphrase, token, or other private information.
Authorization: Determines that the proven identity has some set of characteristics associated with it that gives it the right to access the requested resources. Access Criteria can be thought of as: Roles, Groups, Location, Time, Transaction Types.
IAM as a process
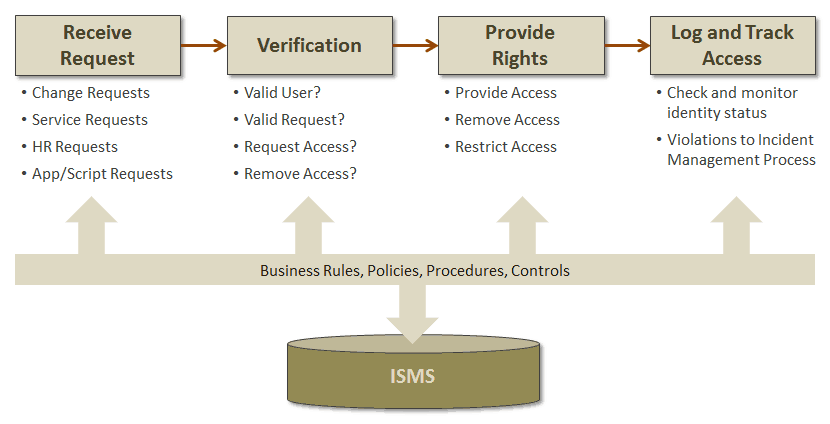
IAM grants authorized users the right to use a service, while preventing access to non-authorized users. As seen in the model above, this process cannot effectively contribute to business value without other processes (i.e. Security Management), where Security Management sets the policies for the process, IAM receives requests, verifies identity, and provides/revokes rights based on those policies. If you are struggling with thinking of this as a process, turn to the IT Infrastructure Library (ITIL) to help out, particularly the 2011 version where access management is further described in the Service Operation volume. The general process steps and key activities include:
Since IAM exists to protect the assets of the business (information), the value of having a well-constructed and managed process is paramount. When deployed correctly and efficiency, IAM can yield many benefits, notably:
- Compliance with various regulatory requirements (SOX, etc.)
- Allow the organization to maintain effective confidentiality, availability and confidentiality of its information.
- Employees have the right level of access to do their jobs.
- Data entry errors reduced by not allowing improper or untrained staff to use a service.
- Increased audit capabilities to trace abuse.
- Timely and effective revoking of access.
Identifying Meaningful Controls
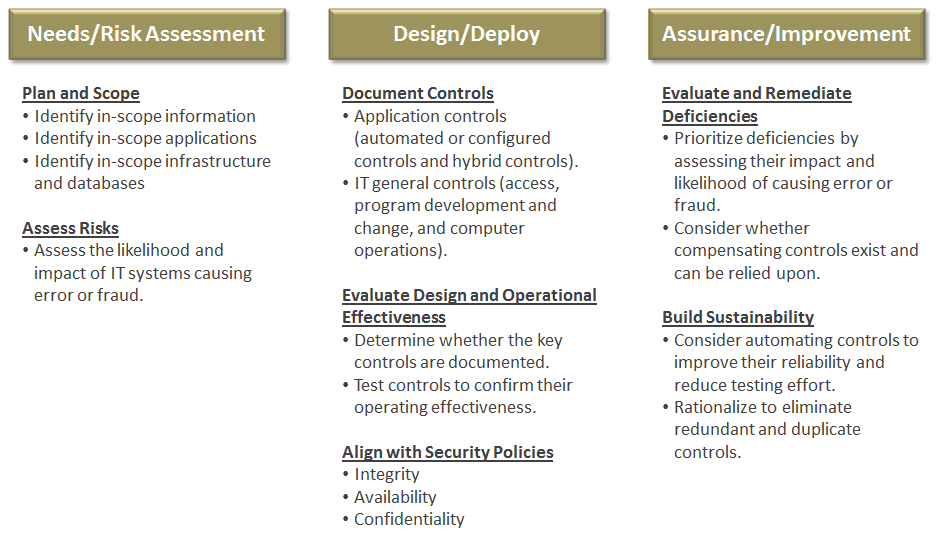
From a management perspective, it is not enough to simply pick several controls that you think are the best fit. Start by understanding the needs of the business and how you will balance performance and conformance. By starting with the business needs and the priorities, you can map, or cascade the needs using a risk based approach and determine the most meaningful controls. I’ve found that using the COBIT Framework by ISACA (particularly COBIT5, the latest release) as a very solid approach to this. In addition to linking goals to processes to controls, there are multiple mapping documents that link to SOX, ISO27000, COSO, etc. Below is a simple three phased approach to get you started:
Some of my final thoughts…
- IAM is a process that is separate from the Security Management process: Security Management sets the overall policies for confidentiality, integrity, and availability while IAM executes those policies.
- IAM is less about the technology, and more about enabling the business (although products are absolutely necessary), information security should understand and influence this.
- IAM should be delivered as a deliberate program, with formal communication, not a set of loosely connected projects and should have business analysts to help define needs and requirements.
- Most IAM challenges are not technical — they are often related to weak process management.
- A risk management approach must be taken towards all IAM projects.
- Service desk staff must understand and follow the process when dealing with users and customers via the Request Fulfillment process.
Good luck in your deployment! As always, your thoughts and feedback are appreciated!
Mark Thomas – Director of Business Services
Interface Technical Training
You May Also Like
Access Management, COBIT, COSO, Identity Management, ISO27000, IT Controls, ITIL, Security Management, SOX
A Simple Introduction to Cisco CML2
0 3894 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 642 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 725 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments




See what people are saying...