Cisco EIGRP authentication – what is the key?
Cisco EIGRP authentication – what is the key?
How many times have you heard that two potential EIGRP neighbors with md5 authentication configured will neighbor up even if they are not using the same key in their key chains? Several Cisco texts have made this comment. I decided that I would put this to the test. I configured some real routers and I duplicated the test with GNS3. I got the same results every time I tried it; that is, the neighbor relationship would break if I used mismatched keys. So even though claims are made that the routers will cycle through the keys in each one’s key chains until it finds a matching key, let’s see what really happens. In both my real environment and in my GNS3 environment, I have two routers connected via their FastEthernet 0/0 interfaces on a 10.1.1.0 network. I have configured EIGRP and configured the following network statement on each:
1 | network 10.1.1.0 0.0.0.255 |
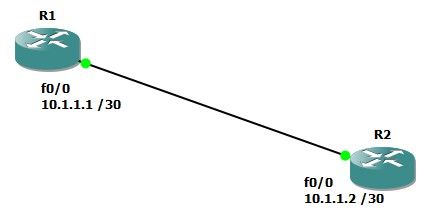
It is a very simple network and it looks like this:
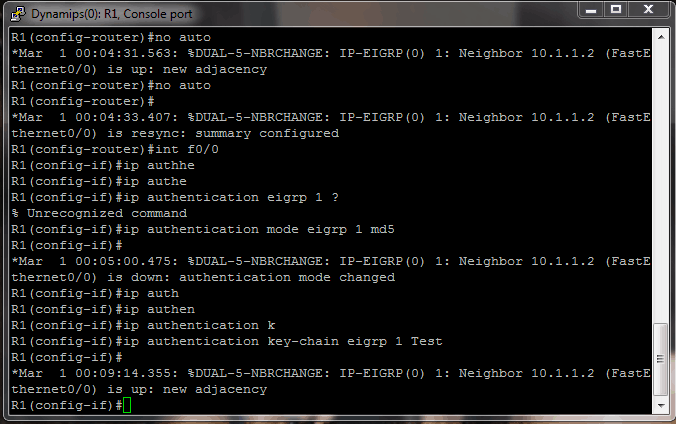
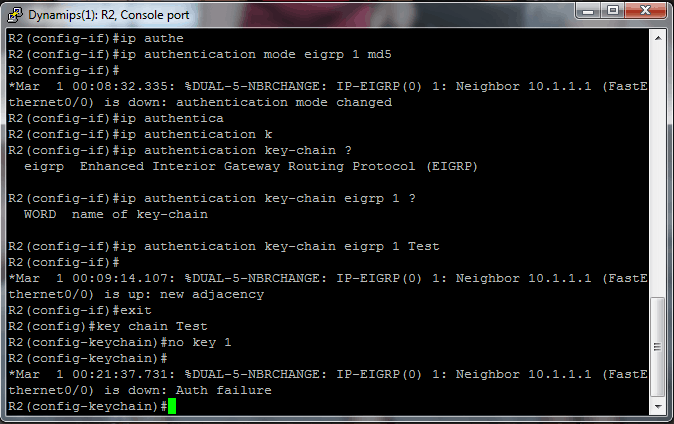
I have created a key chain named Test and keys with IDs of 1 and 2, with key-string values of key1 and key2, respectively on each router. With all this in place, I see the neighbor relationship built and maintained successfully, as shown below.
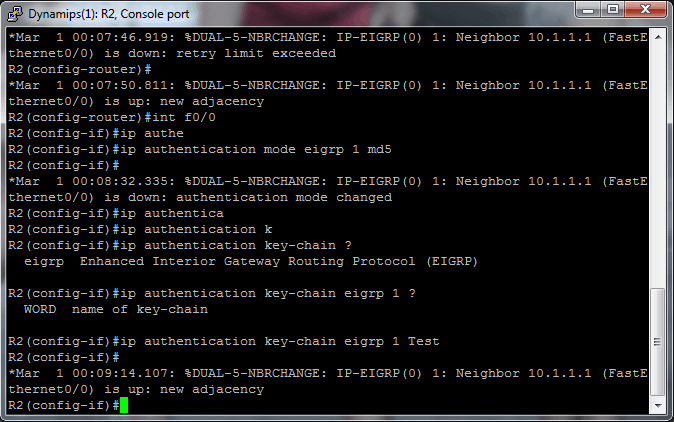
Now the goal is to try to verify that changing the key configuration will not break the neighbor relationship. For instance, I will go to R2 and delete key 1. Watch what happens…
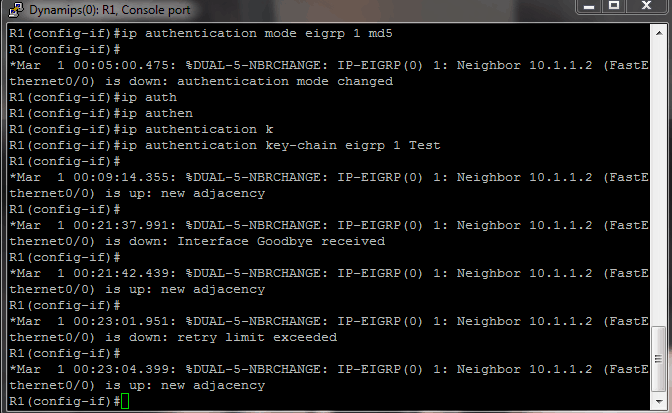
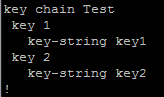
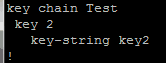
R2 drops the neighbor immediately with the message “Auth failure.” R1 drops the neighbor, but then re-establishes the neighbor relationship. It subsequently dies and is reborn repeatedly. The two key chain configs side-by-side look like this:
 |  |
|---|
R1 R2
This example shows that even though both routers agree on key 2 and the key-string value for key 2, authentication does not function correctly and the neighbor relationship is not stable.
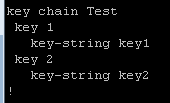
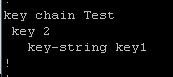
Let’s try another one. Here are the configs:
 |  |
|---|
R1 R2
Once again the neighbor relationship fails to form, even though the string value of key 2 on R2 matches the string value of key 1 on R1.
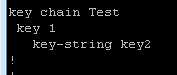
Let’s look at one more example. Here are the configs:
 | 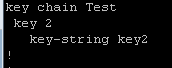 |
|---|
R1 R2
In this case we have matching key-string values but different key numbers. Once again, the neighbor relationship fails to form.
The lesson we learn here is that when configuring authentication for EIGRP, make sure both the key id value and the associated key-string values match to ensure the formation of EIGRP neighbors.
If you have found a way to have mis-matched key values and still form neighbors, I would love to hear about it.
Happy authenticating!
Mark Jacob
Cisco Instructor – Interface Technical Training
Phoenix, AZ
You May Also Like
authentication, CCNA, Cisco, EIGRP, key chain, key-string, md5, mismatch
A Simple Introduction to Cisco CML2
0 3896 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Cable Testers and How to Use them in Network Environments
0 727 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments
Data Models in Business Analysis
0 200 0This video is from our PMI-PBA Business Analysis for IT Analysts and Project Managers (PMI-PBA)® Certification now available at Interface Technical Training. Also see Steve’s PMP Project Management Certification Course: Project Management Professional (PMP®) Certification Video Training PMBOK® 6th Edition Video Transcription: Data Models are part of the elicitation analysis in PMI-PBA. This is the way … Continue reading Data Models in Business Analysis