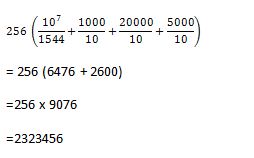Cisco Live 2012! What a week I had!
Cisco Live 2012! What a week I had!
I can breathe again! I just got back from an incredible experience – Cisco Live 2012 in San Diego, California. First of all yes, the weather was absolutely magnificent. It was 70° and breezy. The lure to remain was powerful, but alas! my life called me back. I will mention some of the highlights first, then go back and get into a little more detail on some of the specifics.
The keynote address was introduced with energy, pounding hip music, and stunt bicycle riders. It was enough to thrum the more than ten thousand person throng (actual attendance was estimated at 17,000+) into a frenzy. Carlos Dominguez, senior vice-president and technology evangelist, managed to sneak onstage atop one of the stunt bicycles. The theme of the address was: “What You Make Possible.” To launch the theme, he announced that at the Cisco Live event, six people became CCIE certified, showing us that, yes; it is a goal that is reachable!
He then introduced Padmasree Warrior, CTO and Cisco’s co-leader of Engineering. She began with a strong prediction: “We are on the verge of perhaps the most significant change the IT industry has gone through in several decades.” She then laid out Cisco’s vision of how they believe networking is going to change in the next five to ten years, especially regarding three key areas: security, mobility, and cloud. One driving force in these changes is the prediction that, similar to Moore’s law which states that the number of transistors on a chip will double approximately every two years, the size of the Internet will double every 5.32 years. She stated that 70% of all enterprises will be using some form of enterprise cloud computing by the end of 2012. All this means that the face of IT is changing, and IT professionals, together with industry leaders, either get on board, or get left behind.
Some of the other buzzwords and phrases mentioned throughout the week were BYOD, CONE, LISP, Prime, programmable intelligent network, and others. The BYOD concept refers to the fact that many more mobile devices are attaching to the internet, and thus company networks, in droves. The question presented was, “Is your company’s network infrastructure designed to support this access, while maintaining throughput and providing for security as well?”. The acronym stands for Bring Your Own Device, which is what everybody seems to be doing at work and everywhere else. Regardless of mobile platform, Cisco is positioning itself to provide companies with the end-to-end network infrastructure to accomplish this goal. LISP, or Locator/ID Separation Protocol, was demonstrated during the opening day keynote address. The goal here was to separate one’s physical location from the device on the network and allow you to move around freely and stay connected to the network. Even the location of a virtual server can be changed without losing connectivity. It was compared to local number portability in the voice network arena. It allows a user to get one IP address and then never have to change it. Interestingly, Cisco owns no patent on this LISP concept, they have released it into the public domain because Cisco feels that it is important for future applications to have this capability.
Also presented was Unified Access using the model of One Network, One Management, One Policy. This allows a person, such as a doctor, to use a mobile device of his choice to connect securely to the company (hospital) wireless network and be granted access to the applications he needs to do his job. Because he is found to be in a trusted network, it all works seamlessly. The joining of the corporate wireless network also includes a contextual policy, and in the example of the doctor, he is allowed access to information such as electronic medical records. Records such as these are protected by laws which govern their accessibility. In other words, if an authorized person is attempting to access this information from an untrusted network, access should be denied. In our example, access is granted because he is on the company’s trusted internal wireless network. The Identity Services Engine, which is functioning as the policy server, recognized our user, connected him to the applications to which he should have access, is aware of the device he is using, and the location from which he is accessing the network. It does not matter if this access is happening wirelessly or over a wired network. Now if our doctor leaves the hospital and goes to the local coffee shop and joins their network, he can continue to stay in contact with the hospital and some of his applications. But if he attempts to access medical records, the roaming policy of the hospital causes him to be denied, because these are protected records.
Cisco Open Network Environment (CONE) leverages three pillars of what Cisco deems to be their strengths, and each pillar is a pair that works together. The pillars are Hardware + Software, Physical + Virtual, and Network + Compute. The first pillar involves the release of new APIs which cater to the developers in the networking world. This ties in with what Cisco feels will become more and more important in the near future, and this is network programmability. This strategy is also focused on Cisco’s desire to increase its customer base in the virtual networking world. She mentioned the NX-OS 1000V, which supports virtualized networking components and is being made more multi-hypervisor capable.
I could go on but if you want the nitty gritty details (and you have a Cisco.com login) you can view many of the sessions online at Cisco Live 365. If you were unable to be in attendance, you can relive the experiences of the keynote addresses, interviews, and occasions where Carlos (Dominguez) ran around with a camera crew and got people to comment on a wide variety of fun topics.
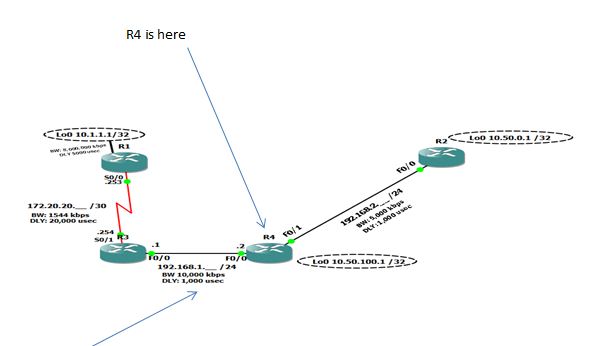
My absolute highlight came while at a session conducted by Pete Lumbis. He was presenting on the topic of routing using EIGRP. I have had a question regarding some results I obtained in a small lab environment, and several posts to online forums yielded no results. Nor did an exhaustive search of web pages (that’s not to say an answer is not there, just that I did not find it). Anyway, I asked Pete after the session if he could determine why a certain output was showing the way it did. He took one look and answered within a few seconds. I was amazed. If you are curious, the lab topology and results are shown here:
This is what I asked Pete:
I can see how the results in parentheses were obtained from the simplified K-value formula:
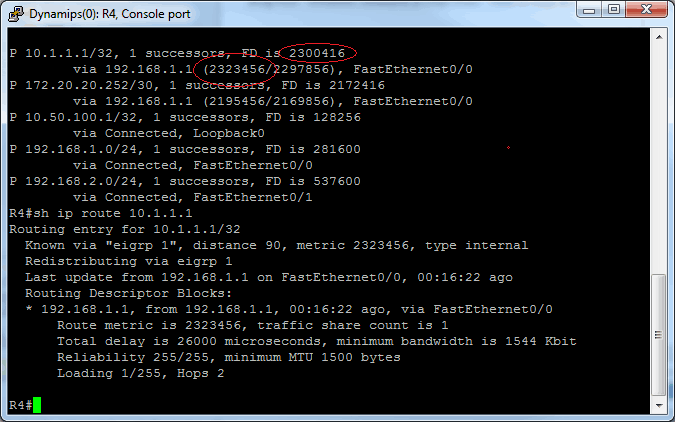
But from where does the 2300416 come?
Pete’s answer was that a convergence event has occurred, but that DUAL (Diffusing Update Algorithm- EIGRP’s ‘engine’) had not run after its occurrence. Simply run the following command on R4:
clear ip eigrp neighbor
This forces DUAL to run again. Then execute the same command that generated the output shown in the R4 windows above, which is
show ip eigrp topology
and you will see the two values match. That was so cool to finally have that question answered. Another thing I learned at the Cisco Learning Booth might be helpful to those of you studying for an exam. If you have a Cisco.com login, go to The Cisco Learning Network. Once there, click on +ENTRY (or whatever certification level you wish, listed at the top left side of the page). Then click on IP Networking (CCENT) [in our example], then you will have some choices in the middle of the page that look like this:
If you click on the Practice hyperlink, you can go module by module through the material answering practice exam questions. Now they are very clear that the questions here are not the same ones you will see on the exam, but we knew that anyway. Give it a shot!
Lastly, I will say that if this sounds fun to you, start planning now to attend Cisco Live 2013 in June 2013 in Orlando Florida. You will have a blast!
Mark Jacob
Cisco Instructor – Interface Technical Training
Phoenix, AZ
You May Also Like
A Simple Introduction to Cisco CML2
0 3901 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 645 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 731 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments