Deciphering Layer 2 devices and the ARP process
Deciphering Layer 2 devices and the ARP process
So you are troubleshooting the network and PING from one device to another. A reply is received. Great! Connectivity has been restored. But what happened behind the scenes? As long as the two devices are on the same network or subnet, the proof of connectivity never really has to live above Layer 2 (the Data Link layer) of the OSI model. Let’s take a look at what happens to make this PING succeed.
If you have a couple of clients that look like this:
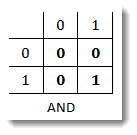
Let’s say the left client, call it client A, is 192.168.1.1 /24 and the right client (B) is 192.168.1.2 /24. If I go to the client on the left and type the command PING 192.168.1.2, I expect a reply. Keep in mind what we know and what we are trying to determine. Since I am typing the IP address, I can say that I know the Layer 3 information, the IP address. I am trying to determine the Layer 2 address, the MAC Address. The client on the left will check his ARP (Address Resolution Protocol) cache to see if there is a Layer 3 to Layer 2 mapping. If none exists, it will send an ARP broadcast to try the locate the destination IP address. Recall that broadcast messages are all ones, which in MAC address format would be all f s (ffff.ffff.ffff). So we can imagine that client B (and any other nodes on this network) receives this broadcast. Then what? For this to make sense, we have to discuss the Boolean operator AND. It turns out that the receiving nodes perform a Boolean AND with the destination MAC address (all 1s) and themselves. Let’s shorten up the MAC address to just four digits to make our example easier to follow. So client B has MAC address 1100, for example, the destination (broadcast) MAC is 1111. A Boolean AND works like this. If the inputs are both 0, the result is 0. If one input is 1 and the other is 0, the result is 0. But if both inputs are 1, the result is 1.
It helps to see it in diagram format:
Let’s apply that to this example. Putting them on top of each other to visualize would look like this:
So the client performs the Boolean operation and Voila! it says, “Hey, this is for me!” because the result of the operation is his own MAC address. Once this happens, it pushes up the information to Layer 3, which then says, “Yep, we are IP address 192.168.1.2. Then client B can respond directly to the MAC address of the sender, since that information was contained in the original broadcast. Once each client has a mapping to the MAC address of the other, a unicast conversation can ensue. Or, in our example, the PINGs will be answered.
ARP information stays in the cache for a default time of 300 seconds, or five minutes, whichever comes first. 😉
This is just a quick rundown of the ARP process, and as I mentioned in my last blog, you can have lots of fun watching processes take place within your network using Wireshark, or another packet sniffer of your choice.
Happy troubleshooting…
Mark Jacob
Cisco Instructor – Interface Technical Training
Phoenix, AZ
You May Also Like
ARP, Boolean, Cisco, Data Link Layer, IP address, Layer 2, MAC address, ping
A Simple Introduction to Cisco CML2
0 3901 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 645 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 731 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments


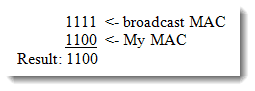



See what people are saying...