Dynamic Name Resolution Services (DNS) and (WINS)
Dynamic Name Resolution Services (DNS) and (WINS)
This content is from our CompTIA Network + Video Certification Training Course. Start training today!
Windows Internet Naming Service (WINS) vs Dynamic Name Resolution Services (DNS)
One of the problems that Network Administrator’s had in the past is, when using static files to do name resolution, as time grows, IP addresses change. Now they would have to go update those files.
If that file is in use on 1,000 machines in a corporate network, we have to go update the file for 1,000 machines. If that machine is out on the Internet, now we have to worry about how to update my files inside the corporate network.
Back in the 1970s through the early 1980s, we used to have to download what was referred to as the HOST file from the University of California in Berkeley in order to be able to resolve names on the Internet.
One of the things that made our lives simpler is to be able to use Dynamic Name Resolution Services, there’s actually two of them.
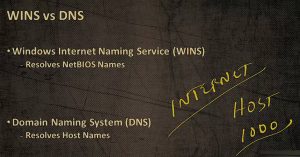
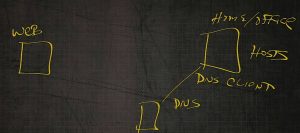
The first one is Windows Internet Naming Service (WINS). It’s used for resolving NetBIOS names to an IP address. This is a user‑friendly name to IP address. Keep in mind, all computers always communicate IP address to IP address. They aren’t going to communicate via the user‑friendly name.
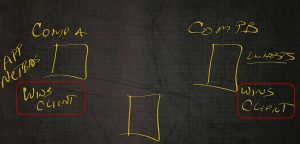
To put this in a little bit more perspective, let’s say we have computer A and computer B.
Computer A has an application on it, that’s NetBIOS stat‑based.
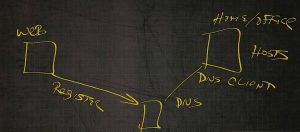
Computer B in order to connect to computer A, will need to resolve computer A’s name to an IP address. We can do that via that static file, with the LMHOSTS file that’s on the machine.
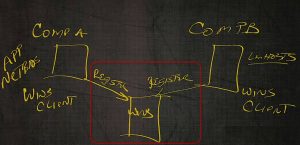
As long as the LMHOSTS file is up‑to‑date, you’ll be able to find the machine or broadcast; “Hey, computer A, what’s your IP address out there?” If that computer’s in another network segment, we’ll never hear it. Something we can do on this computer is set this computer A as a WINS client. And set this computer B as a WINS client.
Then what will happen is computer A will register its IP address with WINS and Computer B is actually going to register its name with WINS.
As part of the name resolution process, computer B is actually going to check WINS and say, “Hey, WINS, do you have an IP address for a computer called computer A?”
WINS is going to give computer A or computer B the IP address for A. Then computer B is going to make that three‑way TSP handshake.
They’re going to be able to communicate and share data with each other. This is the way WINS works. WINS is typically going to be inside of our corporate network only with inside our own organization.
DNS
The number one reason for having Domain Name System (DNS) is if you want to get to the Internet. You cannot get to the Internet without having DNS.
For example, there are thousands of Internet websites out there, and if we’re using the host file, because this is the replacement for the host file we would have to have 1,000 entries in the host file to be able to resolve to the Internet.
This is where DNS comes in handy. Most of the time, DNS is going to be brought into it by our ISPs. We can be able to resolve those hosts‑based names to an IP address. Let’s put into perspective how that works.
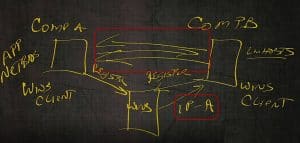
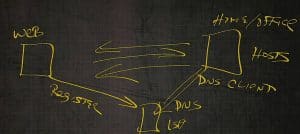
This is a little home computer, office computer or corporate computer. And then on the left is a web page out on the World Wide Web.
We want to be able to resolve to that web page. We’re not a SIG network segment, so will not be able to resolve it unless that IP address was in the host file, which chances are it’s not.
What we will need to do is make this machine here, a DNS client.
Through some mechanism, this machine has to register itself in DNS.
Now my DNS client queries the DNS server. Again, this DNS server could be on‑premise. It could be in your small home office. It could be out on the Internet being usually guided by your ISP.
The DNS client resolves the IP address and performs a three‑way handshake to that client machine.
That web page magically pops up on the side of my computer. We’re going to do full‑blown name resolution in another lesson along with full‑blown use of DNS in another lesson. For basics, that’s how DNS works.
We have the Windows Internet Naming Service files going to replace the LMHOSTS file.
The DNS server is going to replace the hosts file to make our lives a little bit easier, a lot more enjoyable, so we can go home at night instead of having to stay at work and update these files.
Until next time….
Rick Trader
CompTIA Network + Instructor – Interface Technical Training
Phoenix, AZ
Video Certification Training: CompTIA Network +
You May Also Like
A Simple Introduction to Cisco CML2
0 3901 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 645 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 731 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments