Hacking the RSA Wireless Network: Bring Your A Game
Hacking the RSA Wireless Network: Bring Your A Game
I’m attending the RSA Conference this week. Right now I’m writing from the conference floor. The event looks to be amazing, with a great speaker line-up and really strong attendance. I can’t wait for the sessions to get fully underway.
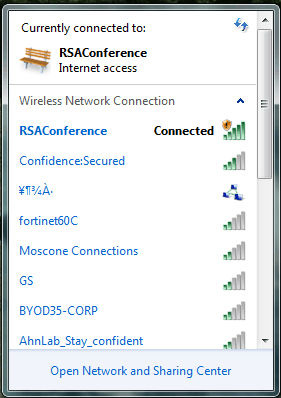
This year the conference is providing free, unsecured wireless networking to all attendees. Yes, free and unsecured wireless access. In this screenshot you can see the official wireless network is the only unsecured network.
Figure 1. An invitation to hackers.
This is pretty darn easy to compromise for most attackers. I’d expect it to be thoroughly compromised in short order. And true to that, there’s an attack being conducted right now.
Sadly, the attacker is simply usurping the wireless network’s SSID. No DHCP server, no DNS server, no traffic redirection. Nothing.
Frankly I’m disappointed. If you’re going to hack the wireless network at the world’s biggest security conference, with the brightest security minds in attendance, at least show the courtesy of engineering a proper attack.
Until next time:
Mike Danseglio -CISSP / CEH
Interface Technical Training – Technical Director and Instructor
You May Also Like
RSA, RSA 2013, Security, SSID, traffic redirection, unsecured wireless, wireless
A Simple Introduction to Cisco CML2
0 3896 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 642 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 727 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments