How Can I Protect My Ports?
How Can I Protect My Ports?
Let your mind wander back in time to the days when you and all your neighbors shared the same piece of the network and you could view their traffic and they could view yours. That was a kinder gentler time in history. You probably can’t even conceive of such a thing happening in this age of increased security awareness and personal information protection. But if you are the network administrator responsible for avoiding the above scenario, how do you go about configuring a solution to such a situation?
The more expensive solution is known as private vlans. However, a company must be running more than just your average switch to configure this solution. What if you work for a smaller company that does not have the resources to purchase switches that support private vlans? All is not lost. There is a less expensive alternative. It is called protected ports. The network admin can provide a functionality similar to private vlans without the considerable investment in high-end networking equipment needed.
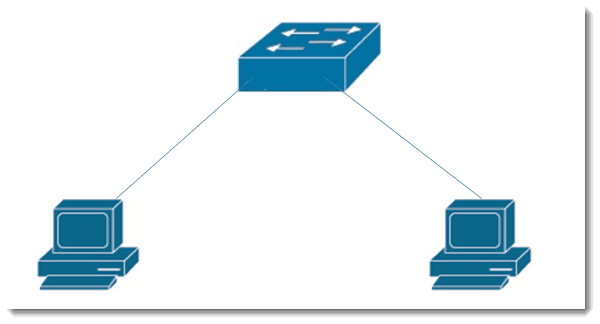
The overall result of configuring protect ports is that host on protected ports can’t talk to each other even though they are in the same subnet. One main difference between private vlans and protected ports is that protected ports are only locally significant whereas private vlan information can be propagated throughout your entire switch fabric. Let’s see what it looks like.
In the above scenario, we have two hosts plugged into a switch. The PCs are in the same subnet. Let’s imagine that the PC on the left is plugged into port f0/1 on our 2950 switch. (Yes, the 2950, as well as the 2960 support protected ports.) Let’s imagine that the PC on the left is plugged into port f0/1 on our switch and the PC on the right is in interface f0/2.
If only interface f0/1 is configured as a protected port, then traffic will still flow between the two endpoints. To cause the PCs not to be able to communicate at all, both interface f0/1 AND interface f0/2 need to be configured using the command switchport protected. As previously mentioned, you will get a result which is very much like using private vlans, but without the expense. To test this, you can assign IP address from the same subnet on the two PCs and generate pings from one to the other. You may want to try your ping test BEFORE you configure your protected ports and then test again AFTER you have configured them. This makes the result of the configuration clearly evident.
It may be that you have never even heard of protected ports. If that is the case, I highly recommend taking some time to familiarize yourself with them. Protected ports are a valuable way to accomplish seeming miracles using a much smaller footprint in your network admin responsibilities. Since the less-expensive, and thus more readily available, switch support this configuration, you can practice using protected ports even in an inexpensive home lab setup. Give it a shot! If this is a new command for you, it is worth getting to know it.
There is no such thing as knowing too many Cisco commands!!
Mark Jacob
Cisco Instructor – Interface Technical Training
Phoenix, AZ
You May Also Like
less expensive switches, limit traffic, private-vlan, protected port, switchport protected, VLANs
A Simple Introduction to Cisco CML2
0 3901 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 645 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 731 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments




Pingback: Cisco Switches - How to Configure Private-VLANs