Video – How To Erase Data Permanently in Windows with Cipher
Video – How To Erase Data Permanently in Windows with Cipher
Most computer users think that when they empty the Recycle Bin, that data is gone forever. Unless the FBI or Interpol decide to use a scanning electron microscope, there’s no way someone can recover the information. Right?
Wrong.
That data is usually still laying around on the hard drive. Data remnants, or pieces of information that you don’t know about, can be on a computer for just a short time. But they can also remain there indefinitely.
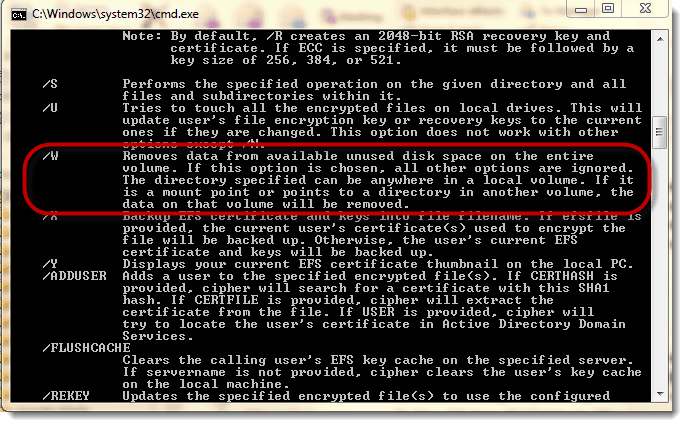
Is there a way to erase the data permanently? Sure! In this video I explain a great feature built into Windows called Cipher /w (the w is for wipe).
Take a look at the video to see why you’d use it and exactly how it works by writing 0’s, 1’s, and pseudorandom hash values to only the unused parts of the hard drive. You’ll see how this erases unwanted data remnants while still preserving the data you want to keep.
Enjoy and be well.
Mike Danseglio -CISSP
Interface Technical Training – Technical Director and Instructor
You May Also Like
CEH, Cipher, cipher /w, cipher switch, CISSP, erase data, Ethical Hacking, IT Security, remove data permanently
A Simple Introduction to Cisco CML2
0 3901 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 645 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 731 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments