More Cisco CCNA Certification Study Tips and Aids
More Cisco CCNA Certification Study Tips and Aids
As you may know if you read my blogs or have been in my classes, I am a big believer in memory aids, or mnemonics. I have a previous blog; Cisco certification exam memory aids – My favorite mnemonics which lists a few of them, but the list is always growing.
One of the things I want to do today is to revisit the EIGRP blog; Cisco’s EIGRP metric – fact and not so fact where I discussed k-values. Perhaps you are looking for a good way to remember which K-value is assigned to which property of the metric. Here is my way: BLDRs is the acronym. Run this sentence through your mind: K-values are builders (BLDRs) of routing tables. K-1 is Bandwidth, k-2 is Load, k-3 is Delay, and k-4 and k-5 are both Reliability (which is why the ‘R’ is plural!). Thus, BLDRs will help you remember these values! \
Another one goes back to CCNA material. If you recall configuring port security on your switch, you may also recall that you have a choice when you assign a violation mode; that is, deciding what you want the port to do if a violation occurs. The three options are shutdown (the default), restrict, and protect. Shutdown is pretty clear – it shuts down the port, and you as the network admin must access the switch and shut/no shut the port to bring it back live again. The other two may challenge you memory, because while they are very similar, there is a difference. Both of the options will cause the port to block frames if a violation occurs, but one of them will increment the violation count, and one will not. Do you know which one is which? The restrict option is the one that increments the violation count and protect does not. How to remember this? I use the vowels in the words to help me keep this in mind. So for restrict, the vowel ‘i’ makes me think of the word ‘increment.’ It also looks like the number 1, so that is how much the violation count is incremented. The ‘o’ in protect looks like a zero, so the violation count is NOT incremented. Maybe this will help you as it does me. Sometimes the silliest things will jog your memory.
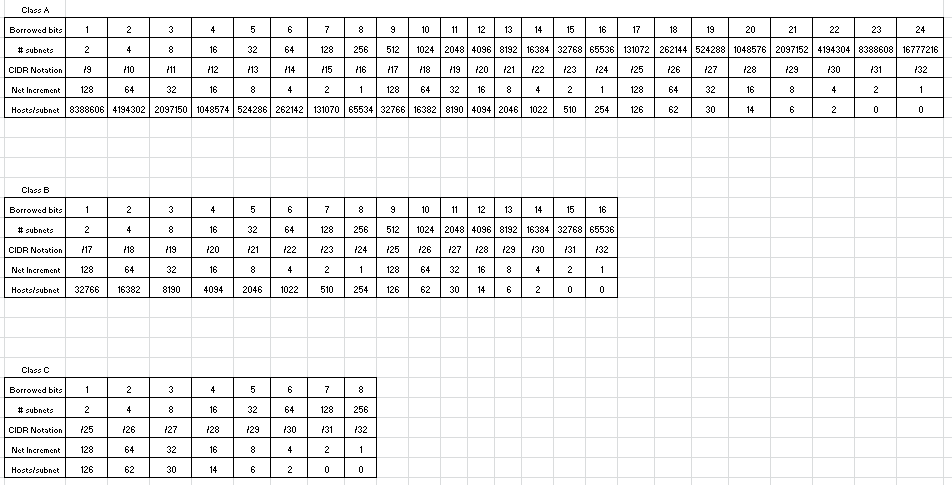
The next thing I want to discuss is a study guide I created for improving your subnetting skills. Of course, you can’t use it on the exam, but it is a great aid to have next to you on the desk while you are running through subnetting problem after subnetting problem. Here it is:
So if you are working a Class A subnetting problem, once you have determined the number of bits to borrow, you can find that number in the top row and see several other valuable pieces of information right in that column. For example, if you are subnetting 10.0.0.0 /8 and you determine that you need to borrow 13 bits, just find 13 in the top row. Below that you see that this scheme will create 8192 subnetworks and each subnet will have 2046 hosts per subnet. You also see that your subnets will be incrementing by 8. Lastly, you also obtain the CIDR notation for the subnets you have created, which in our example is /21.
I hope these suggestions make a difference for a future CCNA candidate as well as maybe even make someone’s job a little easier.
Go get that CCNA!
Until next time…
Mark Jacob
Cisco Instructor – Interface Technical Training
Phoenix, AZ
You May Also Like
acronyms, CCNA, Cisco, EIGRP, exam, guide, K-value, routing tables, subnetting
A Simple Introduction to Cisco CML2
0 3894 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 642 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 725 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments