Planning your Wireless Network for IT Professionals. Can the Access Point Hear You?
Planning your Wireless Network for IT Professionals. Can the Access Point Hear You?
With IT professionals, I’m sure all of us have done things that we’ve been rather embarrassed about and would be considered to be rather silly.
For instructor led wireless training, see our 5-day course: WIRE400: Wireless Networking for the IT Professional
I’m going to share with you one of the funniest things that IT professionals do regarding planning their wireless networks.
It is really common for IT professionals to use the smartphones, the “bars” that are shown on the smartphones, to actually assess whether or not there is WiFi coverage.
We’re going to take a look at why that is a nonsensical thing to do.
Over the years we’ve all been trained by the cellphone industry that when we can’t make a phone call or can’t get data across on our cellphone, that we look at the bars and say, “Are we under coverage or not?” and, “Am I able to communicate with a base-station?” We’ve taken that awareness and started now to apply it to WiFi.
Deployment Scenario
I’m finding that WiFi professionals will take a look at their smartphone and say, “Yes, I have WiFi coverage, and therefore I should be able to connect.” Now, to understand why this doesn’t make sense, let’s look at a deployment scenario.
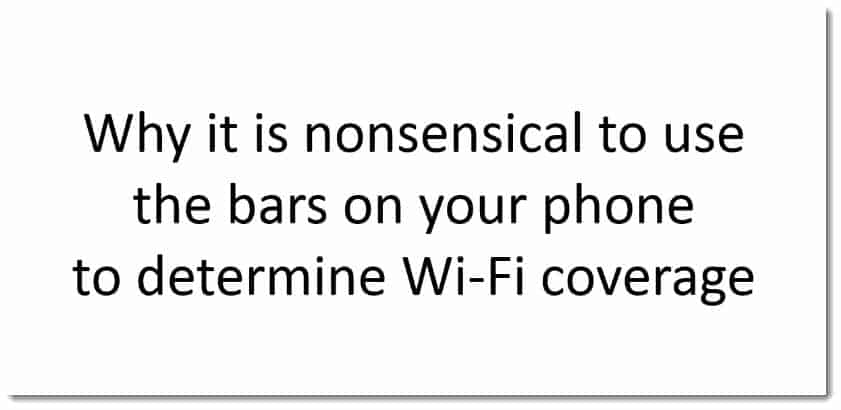
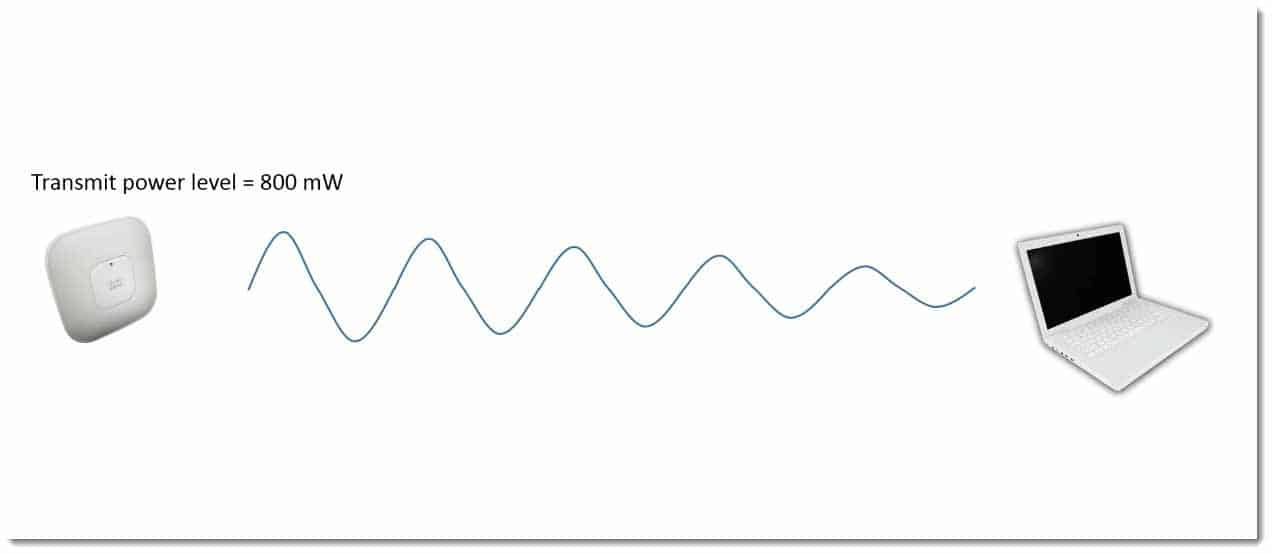
Imagine if you would, you’ve deployed an access point, and in this example we’re going to assume that the access point has been deployed with a maximum transmit power of 800mW (milliwatts). Imagine that we have a laptop that we want to be able to communicate with this access point. When the signals come from the access point to the client, the client can hear the access point.
Laptops are designed to be utilized away from your desk, i.e., not plugged in to the main power. It is therefore fairly common for a laptop to be designed with a WiFi radio that minimizes the transmit power in order to conserve the battery power, and therefore the life which your laptop will continue to operate.
In this example, I’ve set up a laptop and let’s assume that the maximum transmit power is 200mWs. It is still able to hear the access point, but when the laptop goes to respond to the access point and say, “Hey, it’s me. Please, can I connect?”
It cannot transmit at the high power level of the access point, and therefore even though it can hear the access point, when it transmits, the access point is unable to hear the signals from the laptop. It is therefore impossible to establish two‑way communication between the access point and the laptop.
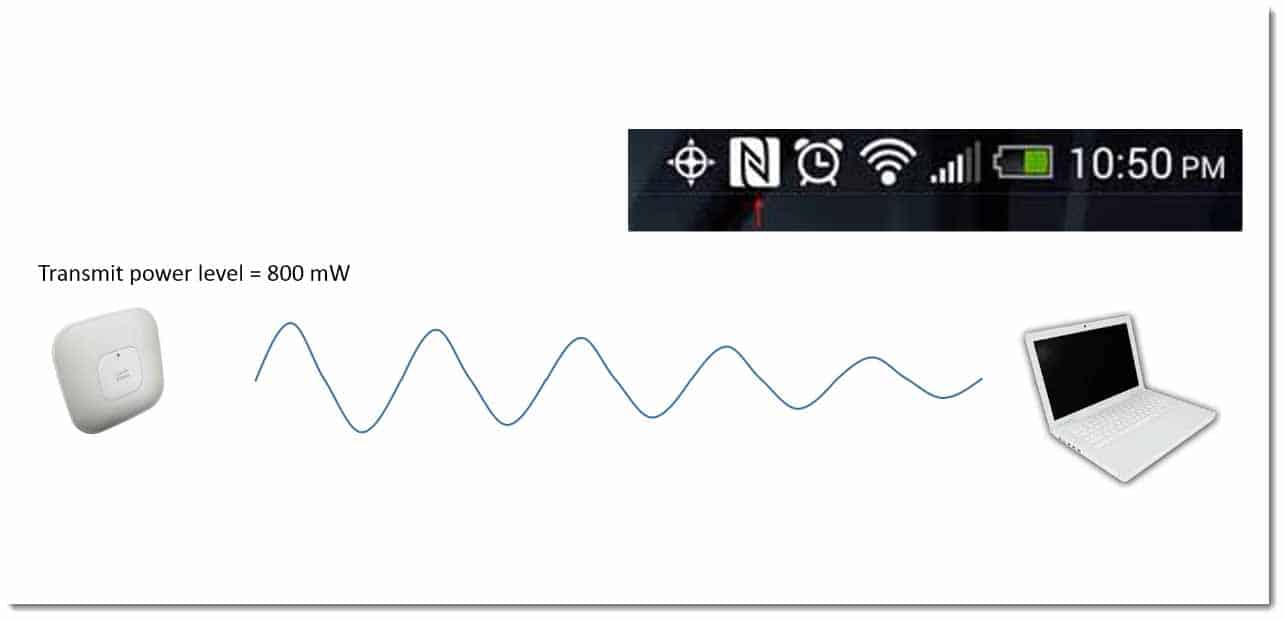
In other words, when you look at the “bars” on your device, what you’re looking at is how well you can hear the access point. What you haven’t done is determine whether the access point can hear your device. It may appear to you that you have WiFi coverage, but in reality you can hear the access point, but the devices cannot communicate with the access point.
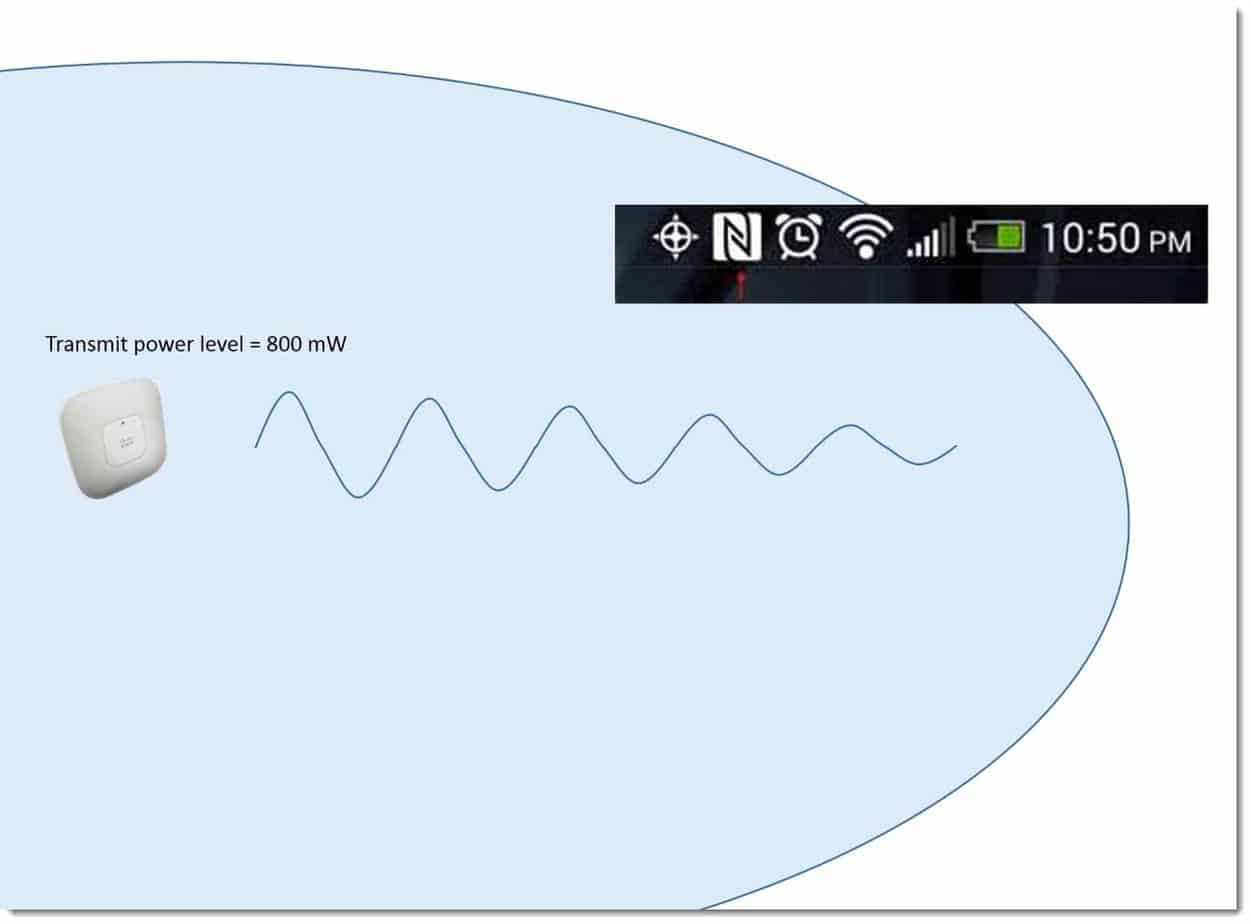
What you might think your coverage looks like this:
In reality your coverage is actually significantly less because your coverage is where devices can form two‑way communication.
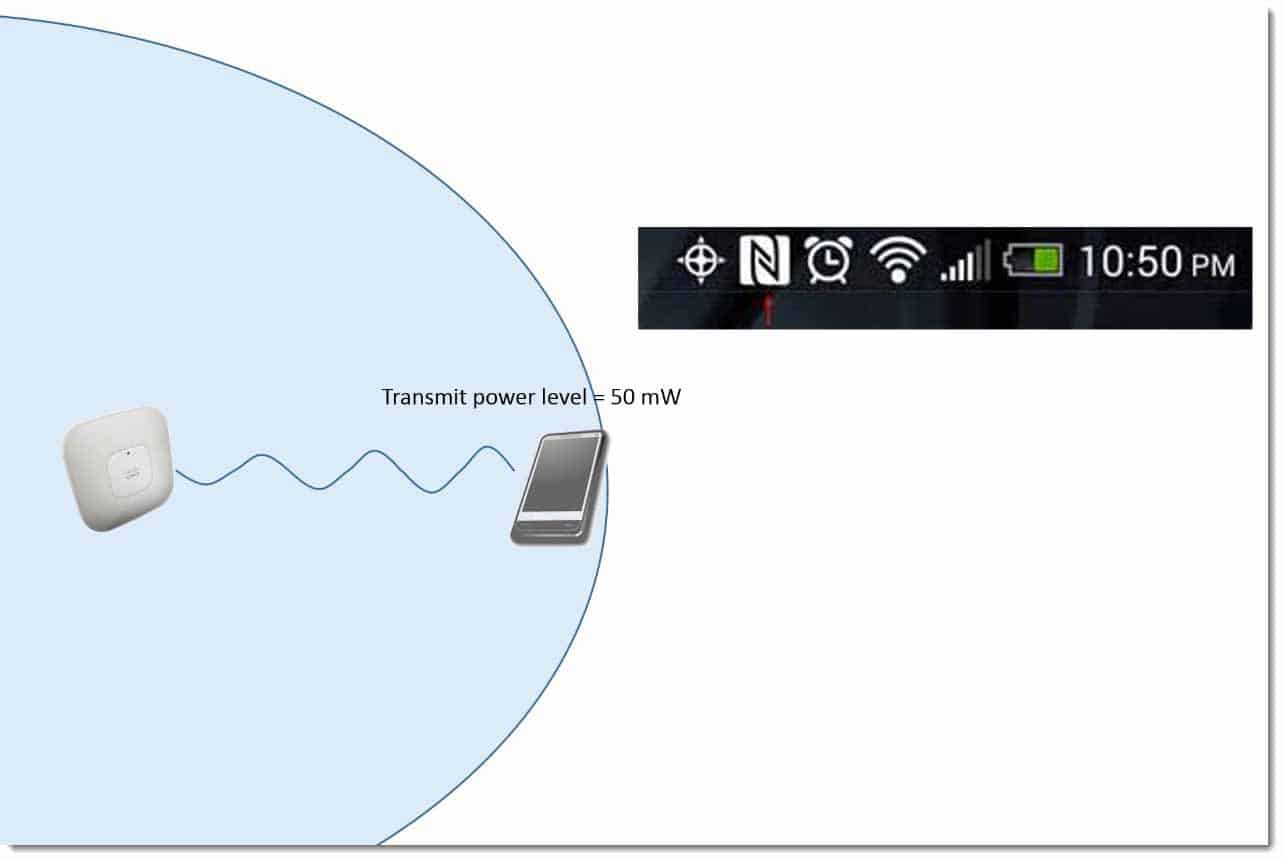
Not just hear the access point, but the access point being able to hear the device. Indeed, if you have devices, such as VoIP devices, some of those have a maximum transmit power as little as 40 mW or 50 mW.
For those devices to be able to connect, they need to be even closer to the access point. In other words, when you’re planning out a WiFi network, you need to know what the transmit power is of the devices that are connecting to it, and you need to plan around the weakest device that you have connecting to the network.
Just because you can hear the access point doesn’t mean the access point can hear you.
In order to do effective WiFi coverage planning, you must consider communications in both directions. The uplink from the client to the access point is typically always the weakest link because you can always raise the power level of your access point, but you cannot always raise the power level of your client.
If you enjoyed this and now find it quite amusing when you see people trying to do WiFi coverage planning using the bars on their cellphone, then please come and join me for one week of super‑fun wireless training class where you’ll really start to understand how wireless works, how to configure a WiFi network, and how to optimize and troubleshoot it and not make these rather amusing silly mistakes that many IT professionals make today.
WIRE400: Wireless Networking for the IT Professional
5-Day course at Interface Technical Training in Phoenix, Arizona.
Learn how to take control of your enterprises Wi-Fi network. In this 5-day hands-on course, you will learn how to plan, configure, deploy and manage a wireless network, secure and troubleshoot interference sources, identify and analyze Wi-Fi packets in Wireshark for data transfer. This course finishes with an overview of the latest next generation in Wi-Fi product enhancements for enterprise and end-users.
You May Also Like
A Simple Introduction to Cisco CML2
0 3896 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 642 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 727 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments