The Concepts of Switching in CompTIA Network +
The Concepts of Switching in CompTIA Network +
This content is from our CompTIA Network + Video Certification Training Course. Start training today!
Switching:
Let’s explore the actual movement of data across the wire. That concept is actually associated with the device called the switch.
We want to define what a switch is. Especially, you don’t want to go to a job interview, and that’s the first time you ever see an actual switch. A switch is a device that learns MAC addresses and then moves frames. We start with bits and then frames which turn into packets. A switch works with frames.
Switches both physical and virtual switches move frames. I like to imagine a switch to watching a program about this creature called the trapdoor spider. Matching its name, it would build a trapdoor out of sand and webbing, and then hide under it. If something consumable went by, it would jump out and grab it and pull it back in. In other words, it didn’t go hunting. It waited for something to come to it. That’s how a switch operates.
Let’s say that I have a MAC address. We’ll shorten this up so I don’t have to write so much.
MAC address is (A) and MAC address is (B).
You see we’re going here.
Right now, the switch is that trapdoor spider. If I have just plugged this switch in, it’s sitting there doing nothing. It’s not going to go hunt for some data, it’s going to wait.
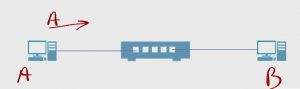
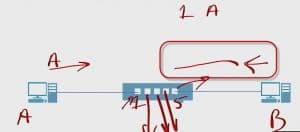
Let’s say (A) wants to talk to (B), which in this network is pretty much his only option. A wants to talk to (B). (A) transmits a frame.
(A) doesn’t know where (B) is. (A) sends out this frame. It gets to the switch. One of the pieces of information that’s here is, “I know my own MAC address,” so when it transmits this frame the switch grabs it.
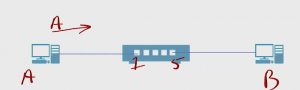
For this example, let’s say it’s plugged into port 1, And (B) is plugged into port 5.
This switch sees the frames and like the trapdoor spider, the switch says, “Ooh, something just showed up. I just got a frame. It’s on port 1. It’s from MAC address (A). Let me write that down in my table”.
So now the switch records in its table on port 1, it now knows about MAC address A.
At this point, that’s the only MAC address this switch knows, so he says, “What can I do? I’ll just send this to everybody.” In this network, everybody is only B. Imagine if there was other PCs plugged in, they would all get a copy of this.
That’s called flooding.
In other words, you can imagine that as a default behavior. If the switch and gets a frame and doesn’t know the destination MAC address, it will just throw a copy to everybody and suggest, “If you’re out there, please answer…”
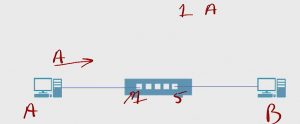
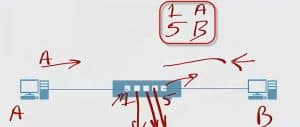
It turns out that (B) was the intended recipient so MAC B replies.
When the frame gets to the switch, the switch see’s it from MAC address B on port 5 and records it into the table, Port 5 has MAC address B.
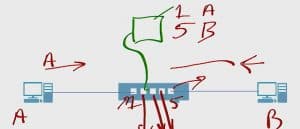
Now, the switch has learned the two MAC addresses of the only two residents of this network. This is how a switch does its job, it listens and learns MAC addresses. Then it move frames based on destination MAC addresses.
From the standpoint of how is this network device useful we could add a network device such as a router which would become the edge of my company.
I could have multiple users on that switch all sharing a pipe out to the Internet. Switching is a very useful concept in networking.
Until next time….
Mark Jacob
Cisco and CompTIA Network + Instructor – Interface Technical Training
Phoenix, AZ
Video Certification Training: CompTIA Network +
You May Also Like
A Simple Introduction to Cisco CML2
0 3896 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 642 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 727 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments