The importance of Security in SCADA Supervisory Control and Data Acquisition Systems
The importance of Security in SCADA Supervisory Control and Data Acquisition Systems
This post if from our CompTIA Security + Video Certification Course, start training today!
Supervisory Control and Data Acquisition (SCADA) has become one of the largest concerns for global Security Officers particular as we automate more populous solutions.
Embedded systems are one area that probably unique to most Security Administrators or Officers that you will need to know for the CompTIA Security + certification exam.
The first of the embedded systems that you need to be familiar with is called Supervisory Control and Data Acquisition (SCADA).
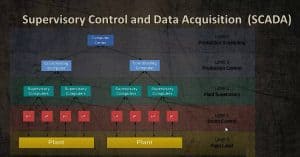
The typical SCADA model is five layers where we have a computer that manages layers of other components. You don’t need to know the five layers for the Security + exam.
Supervisory Control and Data Acquisition Levels
Level 4 – Production Scheduling
Level 3 – Production Monitoring and Control
Level 2 – Supervisory Computers
Level 1 – Industrial I/O Devices
Level 0 – Sensors, Control Valves, etc…
The most-important part to pay attention to is sensors and control valves. These are low-level entries that have some sort of computer processing elements within them. The may not be processors but just controllers such as microcontrollers that maybe on a large motherboard.
Next we have Industrialized I/O Devices to which they connect. And then we move up to the Supervisory Computers and others that connect….
The big deal is with SCADA from a security perspective is the Level 1 systems are typically programmable logic controllers that are given filtering. These could be supporting something like power, oil, water and pipeline distributions etc.,.. In some large cities, SCADA controls the traffic signals for automobiles and pedestrians.
SCADA Concerns:
- Level 1 – Programmable Logic Controllers, Remote Terminal Units
- Level 2 – Customized OS and Software
- Power, oil, gas pipelines, water distribution and wastewater collection systems.
- Easily deployed and repair
- Not easily secured
- Remote Systems access
- Customized software, updates and controls
- Power, oil, gas pipelines, water distribution and wastewater collection systems.
Hackers, particularly terrorists and hacktivists would really love to take over a SCADA system because they could shut down entire water systems, oil pipelines etc…
The challenge behind a SCADA system is they’re easily deployed and repaired by simply replacing components. Because of the layered effect, you could create a cascade problem to occur particularly if you can take over a higher element of the system.
Therefore Level 1 and Level 2 are harder to support because they are customized operating systems and software. When we explore controls and hardening systems you want to make sure you have the latest patches, firmware if it’s hardware elements within the chipset. This can be difficult to deploy if you have a broadly distributed SCADA system with little components scattered across a city or a large geographic region.
Because of the customized software, the updates and the controls necessary to maintain it SCADA has become one of the largest concerns for global Security Officers particular as we automate more populous effecting solutions.
I look forward to seeing you in the classroom or online!
Steven Fullmer
Interface Technical Training Staff Instructor
Steve’s Video Certification Training Classes at Interface Technical Training:
CompTIA Security + Video Certification Course
Project Management Professional (PMP®) Certification Video Training PMBOK® 6th Edition
PMI-PBA Business Analysis for IT Analysts and Project Managers (PMI-PBA)® Certification
You May Also Like
Creating Dynamic DNS in Network Environments
0 642 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 727 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments
Data Models in Business Analysis
0 200 0This video is from our PMI-PBA Business Analysis for IT Analysts and Project Managers (PMI-PBA)® Certification now available at Interface Technical Training. Also see Steve’s PMP Project Management Certification Course: Project Management Professional (PMP®) Certification Video Training PMBOK® 6th Edition Video Transcription: Data Models are part of the elicitation analysis in PMI-PBA. This is the way … Continue reading Data Models in Business Analysis