Securing Your Small Office Systems
Securing Your Small Office Systems
A consulting client recently called me about securing data in their small business office. They are extremely secure already, including data encryption, encrypted offsite backup, locked cabinets and locked data rooms, system account controls and audits, layered authorization, and job separation. Yet they asked a great question – what else can I do to enhance our security?
In an enterprise environment, you might enjoy the benefit of a physical server center, centralized controls like Active Directory and Group Policy, and policies and procedures overseen by trained and certified security staff.
Lacking the time or financial resources of an enterprise environment the security conscious can still perform a self audit of security controls. You don’t need technical training to compare your security elements to broad scale security models. This analysis may not identify ideal solutions, but it will help you generate powerful questions. Look for gaps in your security implementation or perhaps in your understanding. Elements with which you are less familiar become the target – referred to as the ‘attack surface’ – for the malicious intruder. Do a little research. Ask questions of a consultant, or better yet pay for an external review by a credentialed (and trustworthy) security agent.
This blog provides an overview of two common security models that you might use as a starting point: Defense in Depth and Data at Rest/Data in Use/Data in Transit. Review the models as a means to improve your understanding and to develop security questions about your controls. Discussing both within one blog is probably more than a mouthful, though offering two of the many models will provide you insight. You need to look at security from multiple angles, just like a hacker would do, in order to spot and close as many gaps as viable.
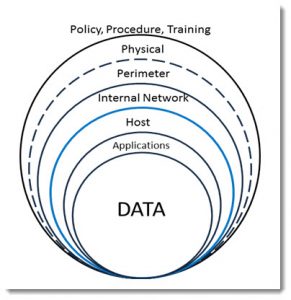
Defense in Depth considers security as a layered model. Depending on my audience, I might refer to the famous Jack Benny’s vault skit from the Lucille Ball show, the opening sequence for ‘Get Smart’, or Tolkien’s walled city of Minas Tirith. The goal is to isolate access in layers. Defense in Depth provides a model for identifying security systems from a layered approach.
Defense in Depth
The most important element of your systems is the DATA. You can recreate your business if the data remains intact and secure yet you lose everything else. Data therefore sits at the core of your security model. Spend most of you resources on protecting your data: isolation, duplication and secured offsite backup, encryption, and controlled access. Ultimately, if your data is secure, your customers will trust that you are doing everything within your power to protect their interests.
Sample Questions:
- How much data do we have and how/where should we store it?
- How can we compartmentalize the data?
- Should we encrypt the data by file, compartment, or entire storage device?
- How do we backup and recover the data?
- Where do we store backups, and how quickly can we retrieve and recover it?
- Who should have direct access to data or data repositories (in raw file form)?
The next layer is the APPLICATIONS you select to access, format, and manage the data. Manage selection of and access to applications and you control how the data is created and maintained. For instance, provide read-only applications for viewing the data, and limit who has write, modify, or delete access. Keep the applications current and patched with the latest security updates. Implement additional applications like anti-malware and logging systems that further protect data integrity.
Sample Questions:
- Do we have an application inventory? How many licenses for each application do we have? Are we tracking the license keys?
- Do we have applications to edit the data, and separate applications to view the data?
- Will customers ever need to view or access the data? What methods will they be entitled to use?
- Who controls application selection, installation, access and use?
- Do the applications have their own security configuration controls and have we set them?
- Are we appropriately updating or patching applications to maintain security?
- Do we have a plan or procedure for review and replacement of application versions when new version releases are issued by the manufacturer?
Applications run on HOST operating systems. Carefully select and maintain your operating system, including implementation and management of security patches, configuration settings, and access controls.
Sample Questions:
- Are we running the latest version of the operating system available?
- Are the BIOS and CMOS settings configured securely?
- Do I have a lock on the system unit or is the system unit secured so that internal drives and cards cannot be physically accessed?
- Have I configured BIOS and/or the operating system to prevent data theft via removable media (CD/DVD/USB) devices?
- Do we prevent the systems from being booted using external media (CD/DVD/USB)?
- Is the Operating System patched to the current level? Are the setting for update acceptance and implementation appropriate, configured, and tested?
- Do we have a plan or procedure to review hardware replacement or refresh? Operating system replacement or refresh?
In addition to considering direct access to computer systems and the data they contain, you need to consider networked access. Both from within your INTERNAL NETWORK and the Internet. Use the most secured and efficient network hardware – from the Network Interface Card (NIC) , through the switches, routers, and modems that provide your infrastructure. Consider isolation of host systems from one another based on purpose or job roles and access to the data they contain. Create guest networks for clients, auditors, or vendors that serve only the most appropriate and desired functions.
Sample Questions:
- Do we have a secured architectural design for our network? Is it documented and is the documentation secured?
- Is each of the network components running with the latest (most secure) versions of the firmware?
- Do we have redundancy built into the network? A fallback plan if an attack drops one or more pieces of the network?
- Have we isolated systems using devices (switches or routers), addressing (IPv4 or IPv6), or host authentication controls?
- Do we encrypt the traffic on our networks (VPN, IPSEC, etc.)?
- Do we have a Demilitarized Zone (DMZ), firewalls, and proxy servers?
- Do we have or need publicly exposed data (Web server, FTP server, email services)?
- Can we place services in the Cloud (Internet) for internal use?
- Have we reviewed all open network or Internet ports, closing the ports or disabling the services that we do not need?
Outside our Internal network is our PERMETER -the means through which data flows into and out of our company. The routers and modems that provide outbound access to Internet tools (Office 365, email), and exchange of information with customers and vendors. These layers are often outside our direct control, so they require contracted Service Level Agreements (SLA) and documented procedures for day-to-day and emergency response.
Sample Questions:
- Does the SLA with our Internet Service Provider(s) cover 7x24x365 support? What does this support enable and have we tested the plan?
- Do we annually review our service providers, their services and their security plans?
- Have we tested soft and hard reset functions for our connections?
- Do we have a plan to continue operations if our Internet connection goes down?
- Are we using the most appropriate and secured tools to communicate to and from our clients?
- Are we legally compliant in relation to data exchange and retention? (Many financial firms must comply with federal regulations that include encrypted, offsite transit and storage of all negotiations and transactions.) Do we know which legal requirements affect our use of security, encryption, and national or international exchange of data?
In addition to all the system layered security concerns, we need to review PHYSICAL security. This layer includes elements like the facility from which we operate; the power and water systems; fire detection, prevention and response. It also includes waste and document disposal (to prevent dumpster diving and theft of personally identifiable information like names, addresses, and phone numbers). From a computer perspective, data is the key element. From a business perspective our employees should be the most important asset. You need to consider their security and safety as well. Parking, lighting, building access during and after hours.
Sample Questions:
- Do we understand and use building access controls? Keys, proximity cards, access pads, automated door locks and closers?
- Does the parking provide adequate lighting, signage, and safe access to the building?
- Does the building provide comprehensive, monitored security systems: fire/smoke/gas detection and alarms; security signage; video monitoring and capture systems; part or full time receptionist or security guards?
- Do we have and have we practiced both lock down and emergency evacuation procedures? Do the procedures protect both people and data?
- Is the HVAC appropriate for both personnel and equipment needs?
- Do we have alternate site or business plans for business continuity?
Finally, no amount of physical preparation can prevent data loss if your personnel are not trained and guided to comply with appropriate security PROCESSES and PROCEDURES. The largest loss or damage to data, whether accidental or intentional, arises from internal sources. You need to consider, design and document appropriate procedures. You also need to review and formally audit them from time to time in order to update them to meet changing needs and environments.
Sample Questions:
- Do we have written or formally created, stored and distributed procedures?
- Do we have documented and controlled security policies and methods?
- Have we provided training to ALL appropriate personnel, including clients and vendors?
- Have we identified external sources to assist with reviews. Audits, or personnel training?
- Have we integrated our policies and plans with building management, local, state and federal requirements?
- Do we have contact for security and law enforcement personnel readily available: police, fire, maintenance, computer support, FBI, computer crime divisions, vendor support?
As you review the Defense in Depth concept and do a little study on your own, you should be able to raise dozens of additional questions, or take any of the above samples toward much greater detail.
The second model, for alternate analysis, is based upon the state of your data.
Data has three forms: At rest, in use, and in transit.
At rest includes its storage state, whether on a local system drive, on a server or network attached storage, or somewhere in the Cloud. You might want to consider which elements of the host, application, and or data should be isolated of exclusively stored locally and which might be stored in multiple locations or in the Cloud. Not all data has, or should follow the same guidelines. You likely have the greatest control over this element, and it the easiest to solve, and therefore most often the focus of security plans.
In use includes creation using an application (Microsoft Office, accounting software, contact databases, CRM and ERP systems, and custom database tools. This includes the authentication, authorization and access control guidelines and tools used to handle data. It also includes the anti-malware solutions use to scan the data as it arrives at the host, while it is resident on the host, and before it is transmitted elsewhere. Control of this form is dependent upon the selection and implementation of your operating system and small business network. While often easy to select, this form takes more effort to configure and maintain. It is therefore too often overlooked.
In transit includes the forms and formats of the data being transmitted, as well as the network infrastructure, protocols, and potential encryption of transmitted or received information. This is typically the state over which you have the least control of data security. Since you might have less control independently, you need to negotiate in transit solutions with third parties. Your customers, vendors and service providers. This is the one area where you can accidentally provide hackers with direct visibility to your data or systems. All they need to do is watch as it passes through the many router hops of the Internet until they discern content of interest.
You might want to revisit the Defense in Depth sample questions while considering impacts on data at rest, in use, or in transit to gain a different perspective.
For yet another model you might consider Colton Matheson’s list from Data Security: 10 Tips for Protecting Your Small Business.
- Identify Sensitive Data
- Control Access
3. Don’t Ignore Mobile
4. Consider the Cloud
5. Encrypt What You Have
6. Hire the Right Help
7. Control Downloads
8. Think About Paper
9. Secure Your Network
10. Update Passwords
There are dozens of other security models. Consider them one at a time. Perhaps during your annual or semi-annual review of security needs. Identify potential weaknesses. Upgrade your policies, procedures, and training. And the systems placed into service to support them.
Or take one of our Security training courses:
IT Security Training CISSP / CEH / CHFI & CompTIA Security + Certification
I look forward to seeing you in the classroom, or online!
Steven Fullmer
Interface Technical Training Staff Instructor
Steve teaches PMI-PBA: Business Analysis Certification, PMP: Project Management Fundamentals and Professional Certification, Windows 10, and CompTIA classes in Phoenix, Arizona.
You May Also Like
A Simple Introduction to Cisco CML2
0 3901 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 645 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 732 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments