You landed here because NISTv2.0 is a replacement for the following:
NISTv1.1: Aligning Cybersecurity and Risk Management Frameworks (CSF/RMF)
Section 1 - Course Introduction
This section will provide an overview of the course including the relevant learning objectives, course organization, and approach. It will introduce the role of the U.S. National Institute of Standards and Technology (NIST) in setting international standards, providing broad risk management guidance, and promoting interoperability.
Section 2 - The Basics of Cybersecurity Risk Management
There are some terms, such as threats and vulnerabilities, that are commonly used but that are also frequently misunderstood. This section sets a foundation for risk management discussion by clearly defining and explaining the terms uses by various risk models, and by exploring the common stages of risk management in public- and private-sector enterprises.
Topics include:
- Internationally-recognized standards and models for describing risk itself and the management of that risk to support enterprise mission and objectives;
- Defining the scope of a risk management program and establishing relevant internal and external context for achieving objectives;
- Purpose and process for risk identification;
- Methodologies and tradeoffs for effective risk analysis;
- Risk evaluation to consider the results of analysis, in light of stakeholder expectations and enterprise context, to determine appropriate risk response;
- Risk treatment through accountable implementation of the risk response selected;
- Monitoring and review of ongoing risk conditions at each organizational level; and,
- Tools, templates, and processes for continuous communications for risk management strategy, direction, achievement, and adjustment.
Section 3 - Introduction to the NIST Cybersecurity Framework v2.0
This section will describe the creation of the NIST CSF and the ongoing evolution of that model to the current v2.0 edition. The course will explain the unique conditions under which CSF was born, why it was included in a Presidential Executive Order, and why it continues to be supported by a collaborative global partnership.
Topics include:
- Events leading to the creation and updates to the Cybersecurity Framework;
- Uses and Benefits of the Framework;
- The CSF process for organizational communications and coordination;
- Framework Components (Core, Profiles, Implementation Tiers); and,
- NIST Supplemental Materials for applying the CSF.
Section 4 - Detailed Review of the Framework Core
This section provides a deep dive into the elements of the CSF 2.0 Core. The Core is what defines the building blocks for planning, building, achieving, and monitoring successful cybersecurity outcomes. Because they are intentionally broad, it is helpful to review their purpose and definition. Because they were developed by committees, it is helpful to hear an insider clarify. The section also highlights some ways that organizations have adapted the Core.
Topics include:
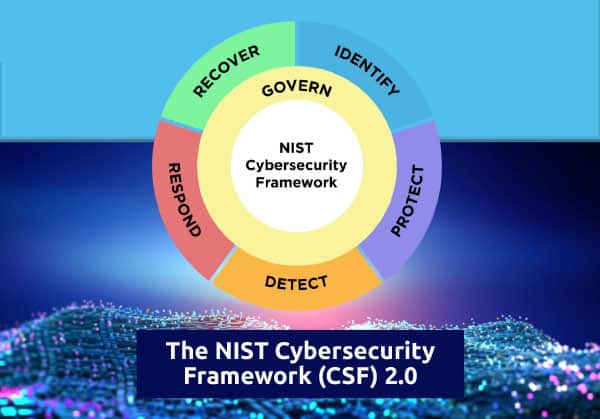
- The Framework’s 6 Functions:
- Govern - Determine and maintain the organization’s cyber risk strategy, expectations, and policy;
- Identify – Determine and document what resources are vital to enterprise mission, and a high-level understanding of threats and vulnerabilities;
- Protect – Define and document how best to protect those resources;
- Detect – Effectively detect and analyze emerging risks;
- Respond – Efficiently implement risk response in accordance with plans, training, and strategies; and
- Recover – Plan, execute, and document steps to recover from cyber incidents, including necessary notifications, communications, and improvements.
- Explore each of the 22 Categories in detail, including review of CSF’s Subcategories;
- Discuss the value of (and cautions regarding) changes to the CSF Core; and,
- Provide a demonstration of NIST’s Online Informative Reference (OLIR) Program.
Section 5 - Organizational Assessment through the Framework Implementation Tiers
The Framework Implementation Tiers are likely the most confused and misunderstood element of the CSF. This section will describe the background for this measurement model, ways that it has been used by various organizations, and potential methods for measuring plans and implementation of cybersecurity outcomes.
Topics include:
- Background and purpose of the Implementation Tiers;
- The components of the Implementation Tiers (Risk Management, Risk Process Integration, External Participation);
- The four Implementation Tier levels (Partial, Risk Informed, Repeatable, Adaptive); and,
- Parallel industry models for measuring process achievement.
Section 6 - Planning and Recording Organizational Outcomes through Framework Profiles
This section will review how to use and maintain various CSF profiles. Profiles represent the most important element of the CSF in that they enable communications about expectations for risk management, current security posture for a given organizational scope, information about risk-related observations, and plans for achieving target milestones. The instructor will share example profiles from NIST and from throughout industry to help students understand how profiles can be adapted and used for many risk management purposes.
Topics include:
- The purpose of the Profile CSF component;
- Examples of manual and automated profiles, including pointers to various templates;
- Discussion about how to measure plans and results;
- Methods for documenting current state (“as-is”), desired, or target, state (“to-be”), and interim milestones between those states; and,
- Considerations for measuring progress and recording that in profiles.
Section 7 - The Cybersecurity Framework Five-Step Process
While the components are a necessary building block for application of the CSF, this section will help to apply the CSF’s implementation steps. These steps have been simplified in v2.0 and provide a process for applying the risk management approach described in Section 2. They build a foundation for an organization-wide cybersecurity risk management program.
Topics include:
- Review of Step 1 - Scope the Organizational Profile.
- Review of Step 2 - Gather the information needed to prepare the Organizational Profile
- Review of Step 3 - Create the Organizational Profile and apply Community Profiles, where applicable.
- Review of Step 4 - Plan actions based on gaps among Current and Target Profiles.
- Review of Step 5 - Implement the action plan and update the Organizational Profile.
Section 8 - Introduction to the NIST Risk Management Framework
This section provides information about the origin and evolution of the NIST Risk Management Framework (RMF). It briefly reviews its origins in security projects for the U.S. federal government to become one of the most-respected risk management worldwide. The instructor will discuss how risk management processes (like assessment, control objectives, and monitoring) change in relation to the portion of the enterprise being managed, and how the risk processes are applied at each organizational level. The course will also explore methods and processes for ensuring effective communications among those levels.
Topics include:
- A brief history of the NIST FISMA Implementation Project;
- NIST's role in various cybersecurity initiatives;
- Introduction to NIST publications and standards;
- The Risk Management Framework seven step process (Prepare, Categorize, Select, Implement, Assess, Authorize, Monitor); and,
- Connections among Cybersecurity Framework steps, RMF steps, and other models.
Section 9 - Integration of CSF and RMF with Other Key Frameworks
This section will provide instruction regarding integration of the various frameworks described in the previous sections with other industry models, including many other valuable NIST frameworks. In particular, the course will include information about NIST’s increasingly valuable work in privacy engineering, and why privacy and security risk management are not equivalent. Materials also The instructor will also demonstrate how the NIST models can be integrated with other industry approaches to support holistic enterprise implementation.
Topics include:
- Integrating CSF, RMF, and the NIST Privacy Framework;
- Understanding the relationship to NIST Special Publication 800-171, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations, which many private organizations must apply in daily operations;
- Defining risk management activities through the work roles, tasks, knowledge statements, and skills statements of the NICE Workforce Framework;
- Leveraging other NIST Frameworks (e.g., Baldrige, Supply Chain, Software Development, Cyber Physical) to ensure a comprehensive risk management approach; and,
- Integrating NIST risk management with those from other worldwide organizations.
Section 10 - Applying NIST Frameworks to Real-World Cybersecurity
This section will conclude the course by reminding the user that frameworks and models provide a type of scaffolding that enables, but are not wholly sufficient, for effective enterprise cybersecurity risk management. The instructor will share industry examples of how organizations are implementing and integrating cybersecurity risk management processes to help transition from theoretical understanding to real-world application.
Topics include:
- Integrating cybersecurity risk management (CSRM) in support of enterprise risk management (ERM), including review of NIST’s recent guidance on that topic (NIST Interagency Report 8286);
- Organizational assessments through integrated CSF/RMF templates
- Processes for security planning through selecting and tailoring security and privacy controls
- Integration of MITRE ATT&CK™ and Pre-ATT&CK into training, assessment, reporting, and monitoring
- Reviewing Roles and Responsibilities from the CSF, RMF, NICE, and other models
- Continuous monitoring and ongoing authorization / ongoing assessment; and,
- Applying the integrated approach to ensure holistic enterprise risk communications, coordination, and comprehension.

