Wireshark reveals Basic Web Authentication flaw
Wireshark reveals Basic Web Authentication flaw
If you spend much time in a position of responsibility within a company’s network, you will likely have need from time to time to stoop down beside the traffic flow and peer inside. A great tool for this task is Wireshark. I want to share a cool thing which can be done with Wireshark. This is not some new untrodden path, but for the up-and-coming network admins who pass my way, this may be something you haven’t seen before.
For an in-depth instructor-led training on Wireshark, see our 4-day course SHARK300: Advanced Network Analysis and Troubleshooting with Wireshark
I want to demonstrate that seeing something with your own eyes often has a longer-lasting impact on your psyche than just reading about it. I can tell you to look both ways before crossing the street, but get your Smartphone slapped out of your hand by a passing car JUST ONCE will forever ingrain in your brain the wisdom of checking for clearance.
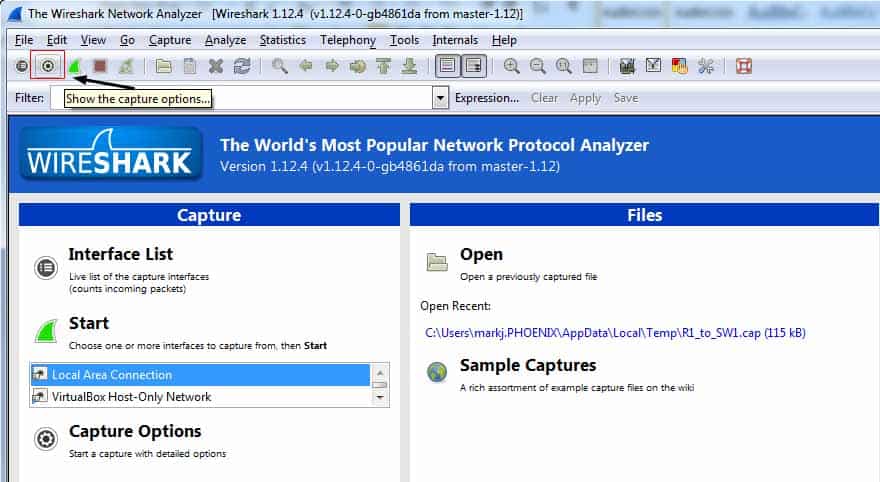
So I want to look upon this with my own eyes (scene: Darth Vader’s helmet being removed) to experience what a lack of attention to authentication strategy can do. I have a web server ready to receive clients. I have a client ready to access this web server. I have a third machine which is just leaning on a shovel. Well, leaning and also monitoring packets (translation: running Wireshark). I have configured a capture filter to include only port 80 traffic, to cut down on the output. To access the capture options, click the icons as shown in figure 1:
Figure 1
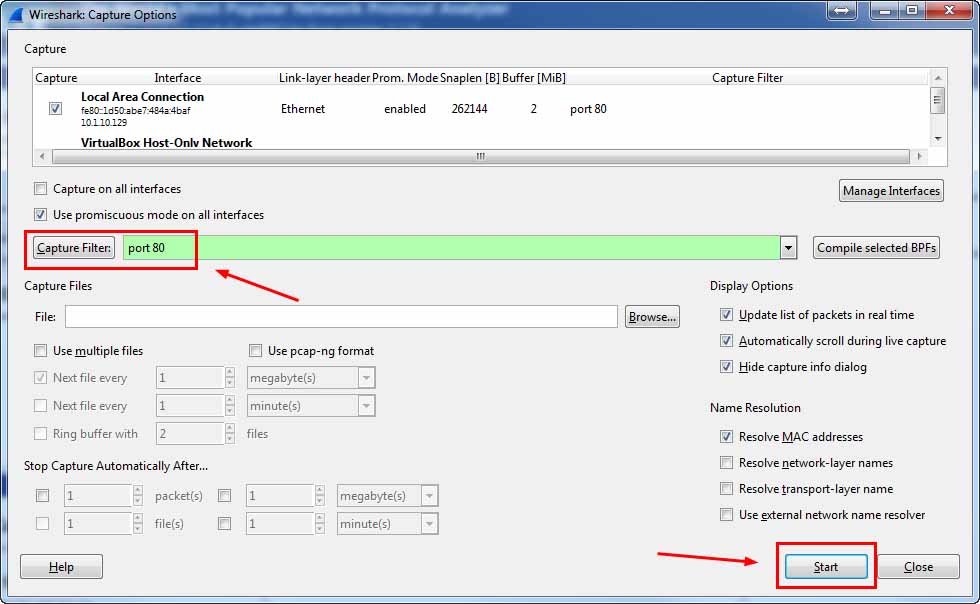
When you hover, it will display “Show the capture options.” In the window that appears, go to the box beside the Capture Filter button and type port 80. Then click the Start button down below to begin capturing only your desired packets. This is shown in figure 2.
Figure 2
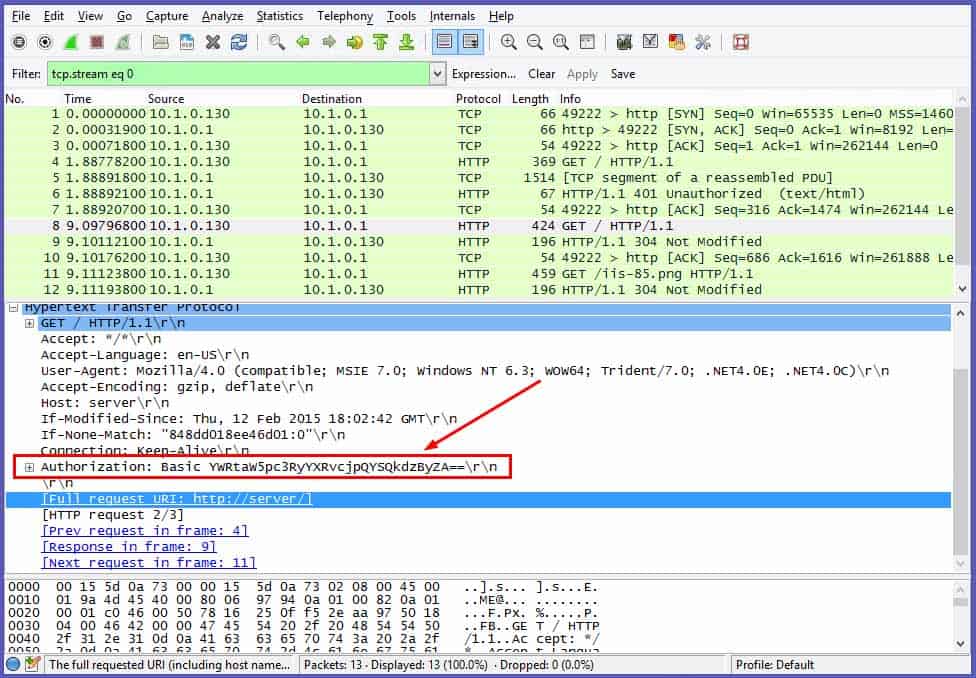
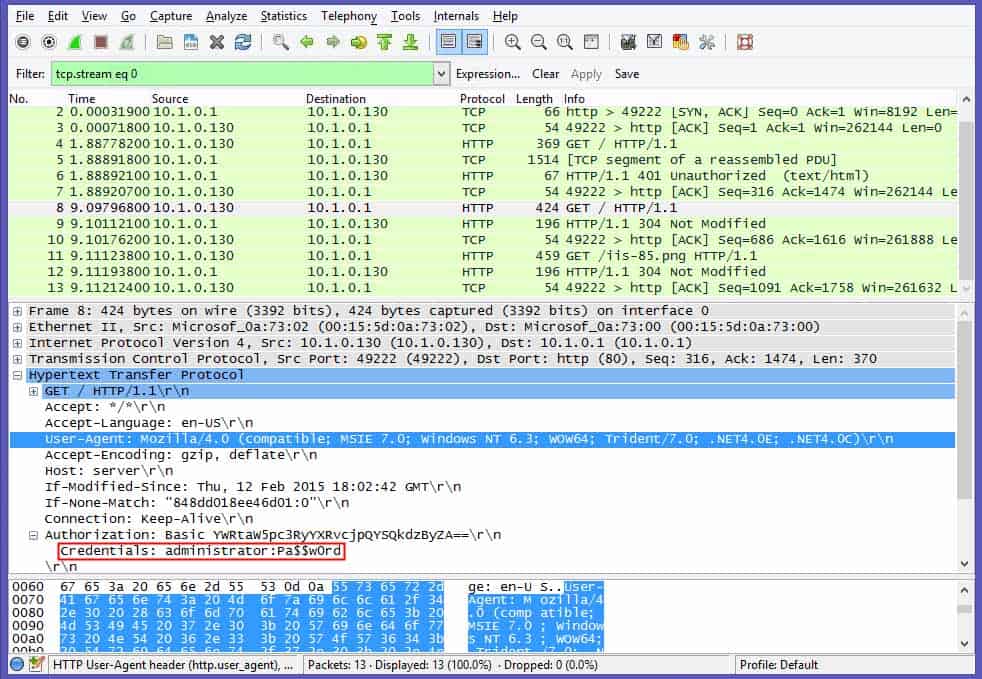
Now that the capture is occurring, I go to my client machine and attempt to browse the home page of my server machine. I am prompted for credentials – username and password. I enter the requested credentials and am granted access. Flip back to my Wireshark box and stop the capture and examine the output. The output is shown in figure 3:
Figure 3
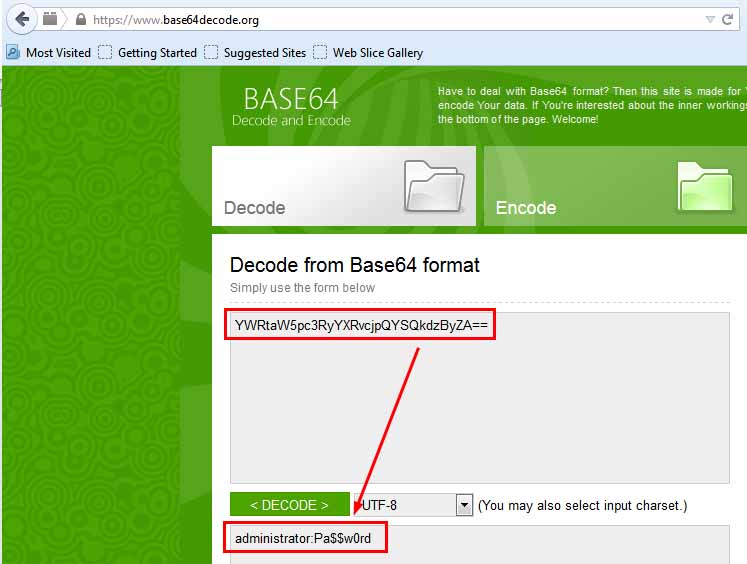
By selecting Frame 8, which contains the Info string “GET / HTTP/1.1, I spy my Basic Authentication piece of this transaction in the window below. Notice the section entitled Authorization. There is an alphanumeric string on the right. If I go to my handy-dandy online Base64 decoder, I can see something quite interesting.
Figure 4
I used base64decode.org, but there are numerous resources available to decode Base64. It’s that easy. However, if that is too much effort, there is an even faster way to see those credentials in clear text. If you re-examine figure 3, you notice a ‘+’ sign to the left of the string I have highlighted. If you expand that, note the result in figure 5:
Figure 5
There are the credentials in clear text, and I never had to exit Wireshark to see them. This shows clearly that Basic Authentication has serious flaws as a web authenticator. As mentioned, you have probably heard this many times, but to see how easy it is to reveal supposedly confidential information is an eye-opener.
I highly recommend gaining experience using Wireshark and in fact, if you watch our course offerings here at Interface Technical Training, we have a 4-day Wireshark class available SHARK300: Advanced Network Analysis and Troubleshooting with Wireshark
Feel free to post any comments about your own Wireshark coolness….
Mark Jacob
Cisco and CompTIA Network + Instructor – Interface Technical Training
Phoenix, AZ
You May Also Like
Base64, basic authentication, clear text, decode, packet sniffer, Wireshark
A Simple Introduction to Cisco CML2
0 3901 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 645 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 731 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments





See what people are saying...