Adding a New Non-Root User in Kali Linux
Adding a New Non-Root User in Kali Linux
Kali Linux is a fantastic operating system for penetration testing and security evaluation. It comes with virtually all security tools built in, it’s lightweight by default, and it has a huge ecosystem that is constantly helping with the project.
For instructor-led Security training see our course schedule.
I created a new installation of Kali Linux recently. One of the first post-installation tasks I did was to create a new user for daily use. Sadly, Kali only creates a default root user during setup. Running as root all the time is a horrible security practice, so I recommend that you create a new user as soon as possible after installation.
To create a new user in Kali Linux, first pop open a Terminal window.
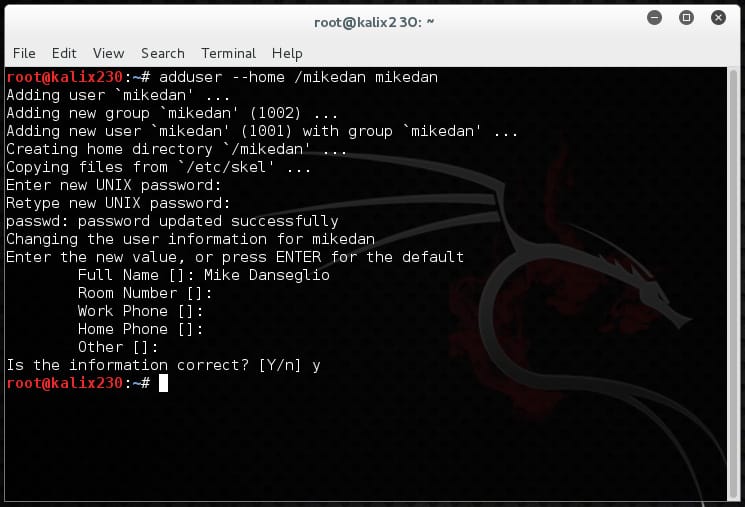
Then use the adduser command. In this example I’m creating a user named mikedan with a home directory of /mikedan so the command is adduser –home /mikedan mikedan.
Adduser prompts for the rest of the information, which is optional.
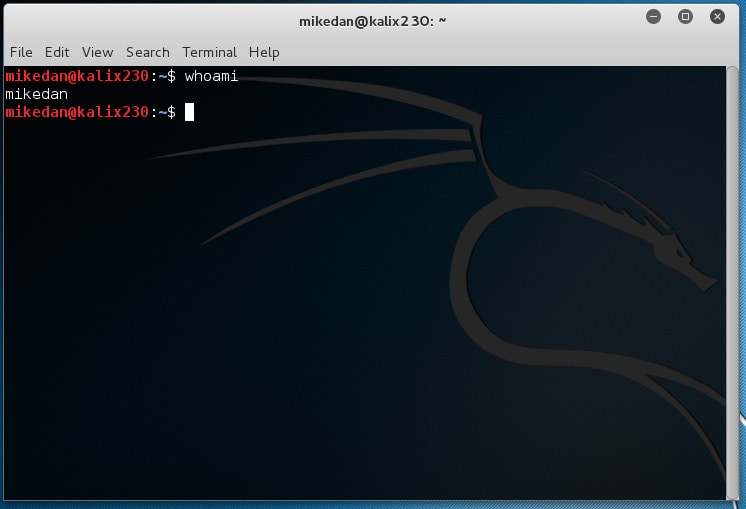
The user account is created. Now I test it by logging out from root and logging in as mikedan. To be sure I open a new Terminal window and type whoami.
Finished! The user account took only a few seconds to create and works as expected.
Enjoy!
Mike Danseglio – CISSP, MCSE, and CEH
Mike Danseglio teaches IT Security Training, Windows, System Center and Windows Server 2012 classes at Interface Technical Training. His classes are available in Phoenix, AZ and online with RemoteLive™.
You May Also Like
A Simple Introduction to Cisco CML2
0 3901 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 645 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 731 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments



See what people are saying...