Concepts of Routing
Concepts of Routing
This content is from our CompTIA Network + Video Certification Training Course. Start training today!
In this lesson, we look at how routers do their job.
Router:
- Moves Packets
- Leans Network Information
Routers move packets. We’ll illustrate this as we did previously with switches.
We have bits – layer 1, then frames (that’s where we have switches) – layer 2. Now packets – layer 3. Routers move packets, switches move frames.
Another distinguishing feature is that MAC addresses are considered hardware addresses, whereas, the packets are IP addresses. Routers move IP, which is a logical piece of information, whereas a MAC address is considered a physical piece of information.
Similar to a switch, it does learn based on what arrives at its interfaces. Let’s take a look at that in greater detail.
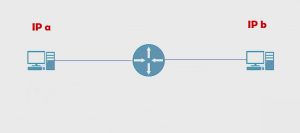
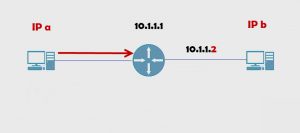
How routers move packets? For example, we have a host, let’s give it a name of IP a on one side and IP b on the other.
This is a direct connect.
In other words, whatever the network is, they both have to be in it. That’s one of the interesting things about routers.
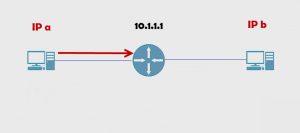
If we have an actual IP address such as 10.1.1.1.
If we try to put 10.1.1.2 on other side of the router, the router will reject that command.
The router is saying, “Wait a minute, these guys are in the same network. 10.1.1.1. You can’t do that.”
In fact, from the standpoint of the router, it could ask you this question and be justified in doing so, “If these interfaces are in the same network, what do you need me for?” The whole point of having a router is to move information between networks.
This is considered one network, and would be considered a different network.
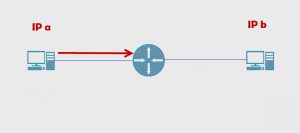
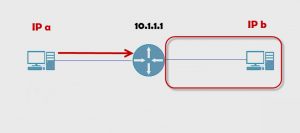
Turns out that IP b this host, cannot directly reach that host because they’re in different networks.
Even if there was a switch here, switches cannot move information between networks, hence that’s why we need this the router in the middle.
It turns out, you could imagine it like if you want to mail a letter to somebody who lives in another state. You hand the letter to the letter carrier because you intend that the post office is going to take that letter and take it to your friend that lives in another state. How would you feel if you handed a letter to the mailman and he said, “Thank you,” and tears it open? You’re like, “Wait a minute, that’s not for you.”
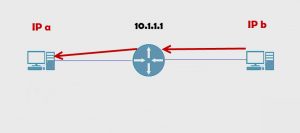
It’s the same concept here. If IP b wants to talk to IP a, IP b hands it to the router. The router realizes it’s not for it and hands it over to the destination. The router has a routing table and as it’s connected and if it’s big enough, there’ll be multiple routers. This router could have various pieces of information in its routing table.
As soon as it gets something from B, it’s going to check the destination and say, “Do I know how to get to A?” In this case, yes, it does. It’s directly connected but the concept still follows. The router checks, “Do I know how to route this packet to its destination? If I do, I send it.”
Interesting, to note, if a router doesn’t know how to route a packet, it drops it. Don’t waste any more time on it. Let it go.
That’s a brief look into how routers move packets.
Until next time….
Mark Jacob
Cisco and CompTIA Network + Instructor – Interface Technical Training
Phoenix, AZ
Video Certification Training: CompTIA Network +
You May Also Like
Define Router, direct connect, MAC Addresses, move packets, packets
A Simple Introduction to Cisco CML2
0 3901 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 645 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 731 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments